Week 3 — Passwords: Storage and Security
Contents:
Week 3 Live Event Section 1: Password Insecurity ---- Video 01: Password Vulnerabilities ---- Video 02: Attacks on Passwords Section 2: Password Storage ---- Video 03: Password Storage ---- Video 04: Unix Password Storage Section 3: Rainbow Tables ---- Video 05: Constructing Rainbow Tables ---- Video 06: Attacks Using Rainbow Tables
Week 3 Live Event


Section 1: Password Insecurity
Password Insecurity
Passwords are simple, useful, and unlikely to fall out of use in the near future. Although password-free authentication may be a superior option for security, it may never become as popular as passwords. In Password Insecurity, we will examine why passwords are insecure and how they are attacked.
Lecture Video Guide
Password Vulnerabilities: Passwords are simple and easy to use–they are also an all-around weak method of authentication. In this lecture, we discuss the strengths and weaknesses of passwords as a means of authentication.
Attacks on Passwords: Password attacks start with stealing the password store (file or database). This lecture discusses why password stealing is possible, and what can find the real passwords after the store is stolen.
Video 01: Password Vulnerabilities
- simple
- insecure, which stems from
- sniffing –e.g.– admin records password, keyboard logger
- phishing (multi-factor authentication is a remedy) –e.g.– fake emails, fake websites
- leakage –e.g.– looking at fingers in the keyboard
- cross-site leakage –e.g.– passwords are reused

Password managers can be used:
- they generate a strong password
- but they are a single point of failure
Video 02: Attacks on Passwords
- password recovery –> inherently insecure
- stealing stored passwords –> cryptographic techniques tries to attack this
- usually done through SQL injection
How to reverse hashes?
- commonly used passwords
- dictionary attacks
- large dictionary of words
- compute hashes
- try breaking in
- rainbow table
- brute force
Section 2: Password Storage
Password Storage
Password Storage addresses effective and ineffective means of password storage.
Lecture Video Guide
Password Storage: Storing passwords in plaintext is asking for trouble. Passwords storage should be hashed. However, even hashed passwords can be reverse engineered with the dictionary attack. Salting the hash may sound strange; this lecture describes why this simple idea makes stealing passwords very difficult.
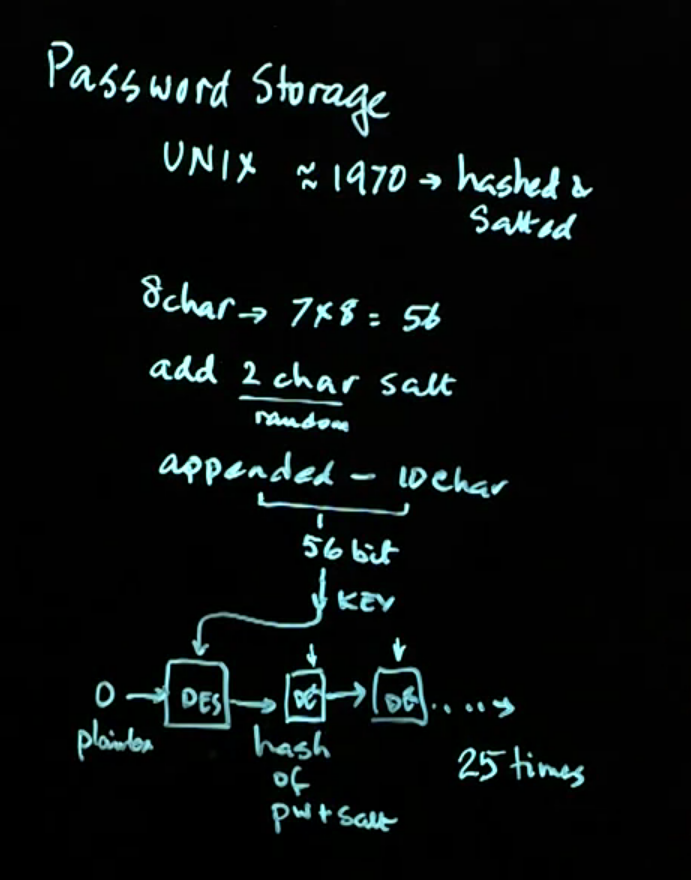
Unix Password Storage: Unix was one of the first systems to use salted passwords stored in a public file (/etc/password). This scheme, implemented in late 1970s, and was simple and secure, and the precursor to the modern Linux password storage system. This lecture describes the evolution from the old Unix storage system and how it has evolved to Linux.
Video 03: Password Storage
- plaintext
- hashed
- hashed and salted
On biometrics:
- no recovery
- stored in plaintext – because every time you scan you get a slightly different image, which needs to be compared so it cannot be hashed
- also called “identity at a distance” vs “identity in person”
Should the password be sent as plaintext to the host or hashed first?
Send as plaintext.
A dictionary attack:
- list of password and their hashes
- can be:
- pre-computed / offline / storage heavy
- on the fly / online / processing heavy
What is salting?
- eliminates a pre-computed dictionary attack
- random data that is appended to the plaintext password prior to hashing
- stored in plaintext
Video 04: Unix Password Storage
What do we use today? (or at least should)

Section 3: Rainbow Tables
Constructing Rainbow Tables: Where dictionary attacks are simple, rainbow tables attacks are powerful and fast. Rainbow tables are an innovative approach to password cracking in terms of time and space requirements. This lecture details how the attack is implemented by rainbow table construction.
Attacks Using Rainbow Tables: This lecture demonstrates how passwords can be captured very quickly once we have created a rainbow table.
Video 05: Constructing Rainbow Tables
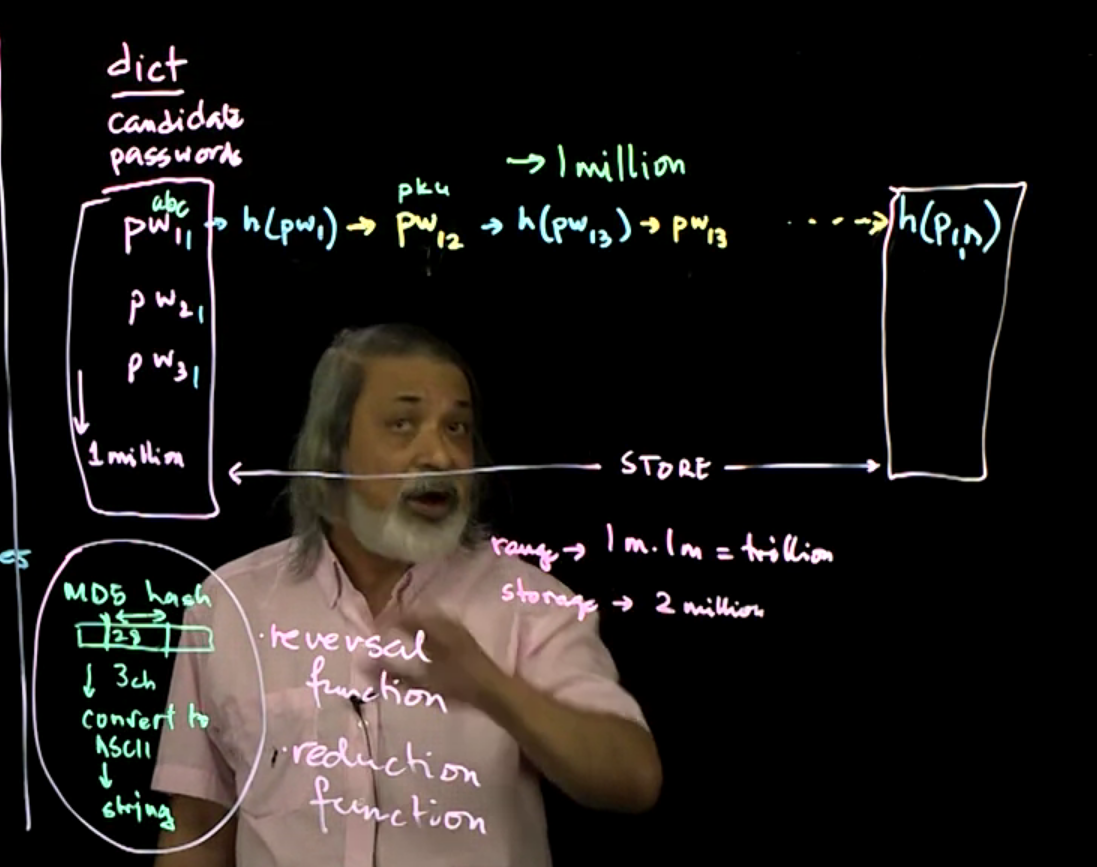
1- Select and store a list of a million candidate passwords.
2- Generate the hash for a candidate password.
3- Use a reduction function to reverse the hash to some password.
4- Repeat hashing and reduction a million times.
5- Store the millionth hash generated, paired with the candidate password.
6- Repeat all but step 1 for the remaining candidate passwords.
7- Save the candidate passwords and hash pairs in persistent storage.
Video 06: Attacks Using Rainbow Tables
maximum coverage = (number of candidate passwords) * (number of times a reduction function is used)
- collisions reduce coverage
- the higher the coverage, the closer you are to brute force
- assume no salting is used
- if salting is used, then you need to re-create the rainbow table for each salt
Note: rainbow tables take around a month to create.
General steps:
- Use the reduction function to generate an intermediate password from the hash.
- Create a hash for the intermediate password.
- Lookup the intermediate hash in the reduction table.
- Get the candidate password if intermediate hash is found in the reduction table.
- Hash the candidate password and repeat reduction and hashing.
- Repeat the reduction and hashing and lookup a million times.
- Stop if the hash is generated in the chain that started from the candidate password.
- Return the password that generated the matching hash.