Week 4 — Authentication, Key Exchange, Public Keys and Man-in-the-Middle (MITM) Attacks
Contents:
Week 4 Live Event Section 1: Authentication ---- Video 01: Authentication and Challenge Response ---- Video 02: Authentication - continued Section 2: Key Exchange ---- Video 03: The Key Exchange Problem Section 3: Diffie-Hellman Key Exchange ---- Video 04: The Key Exchange Problem ---- Video 05: Diffie Helman - continued ---- Video 06: Elliptic Curve Cryptography (ECC) Algorithm Section 4: Public Keys and Applications ---- Video 07: Public Key Encryption ---- Video 08: MITM Attacks ---- Video 09: Digital Signatures and Digital Certificates
Week 4 Live Event







Section 1: Authentication
Authentication
Alice and Bob want to communicate securely. It is important for Alice to verify Bob’s identity and vice versa. Identity verification, or authentication, can be handled in a variety of ways.
Lecture Video Guide
Authentication and Challenge Response: Passwords are a common (and weak) method of authentication. Challenge response systems are a fundamental technique used in authentication. This lecture describes how challenge-response works (using symmetric and asymmetric keys).
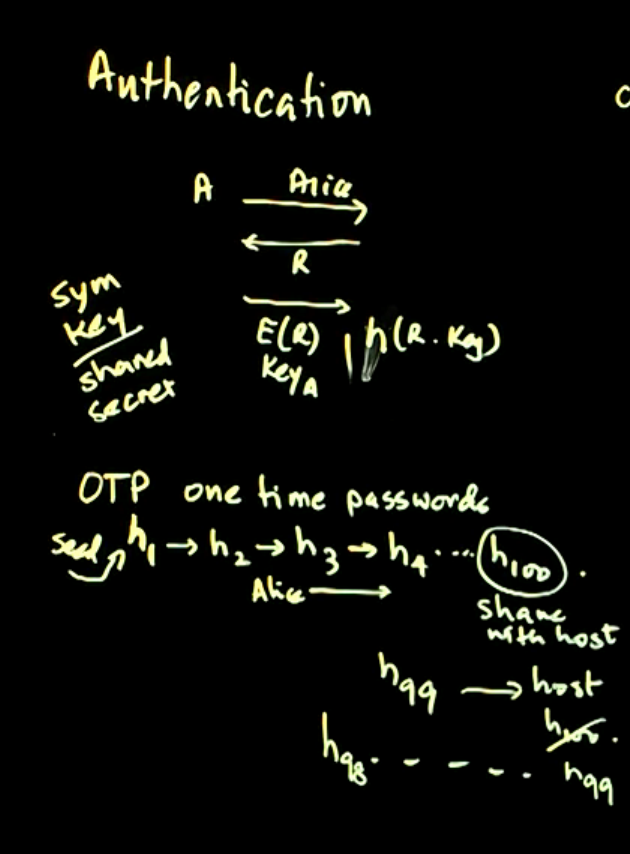
Authentication - continued: This lecture introduces one-time passwords, authentication hardware, public keys and some vulnerabilities of public key challenge responses are described.
Video 01: Authentication and Challenge Response
Authentication is based on each user having a unique set of criteria for gaining access.
client <–> server
- authentication of a client – password
- authentication of a server – PKI (public key infrastructure)
- 2-way auth – both
It is good to use multi-factor authentication:
- what you know – password
- what you have – SMS
- what you are (or can do) – biometric
How to communicate password? (all of the below have issues)

A better approach? challenge-response

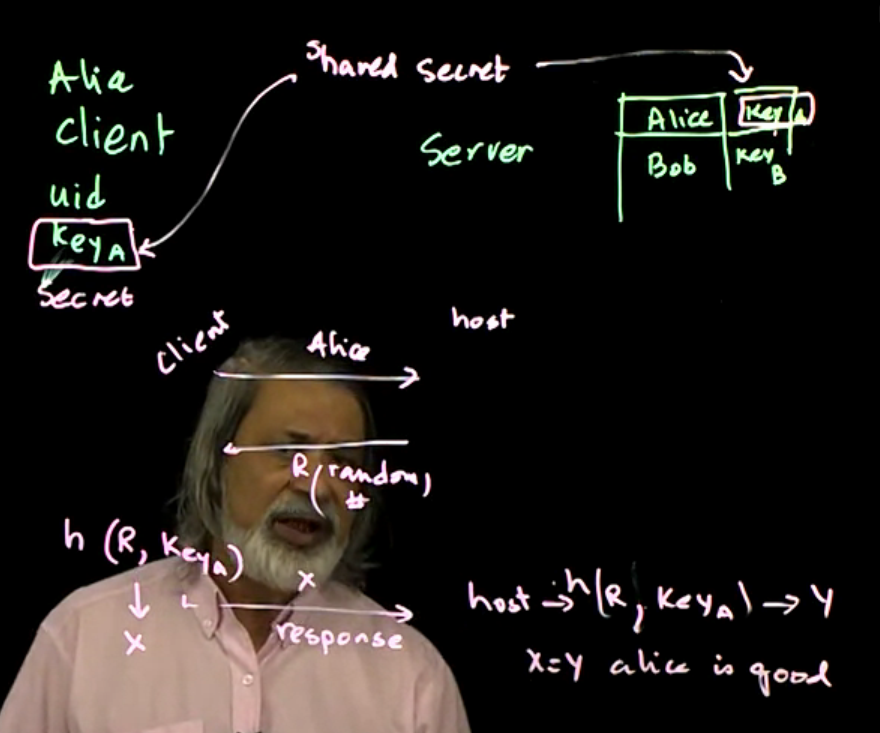
Note: cannot protect against MITM attack.
Video 02: Authentication - continued

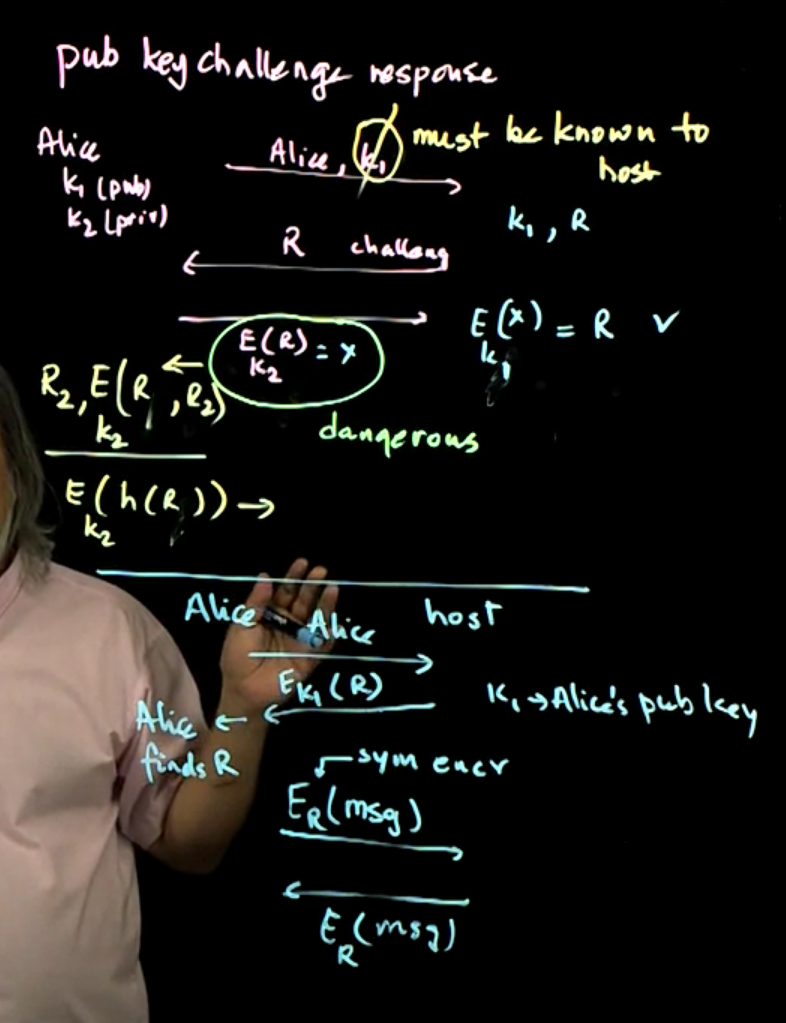
Section 2: Key Exchange
Key Exchange: Alice wants to send encrypted messages to Bob. To do so, first Alice needs to send Bob the decryption key, without using a secure channel. This is the key exchange problem. For a long time it was thought to be impossible to perform.
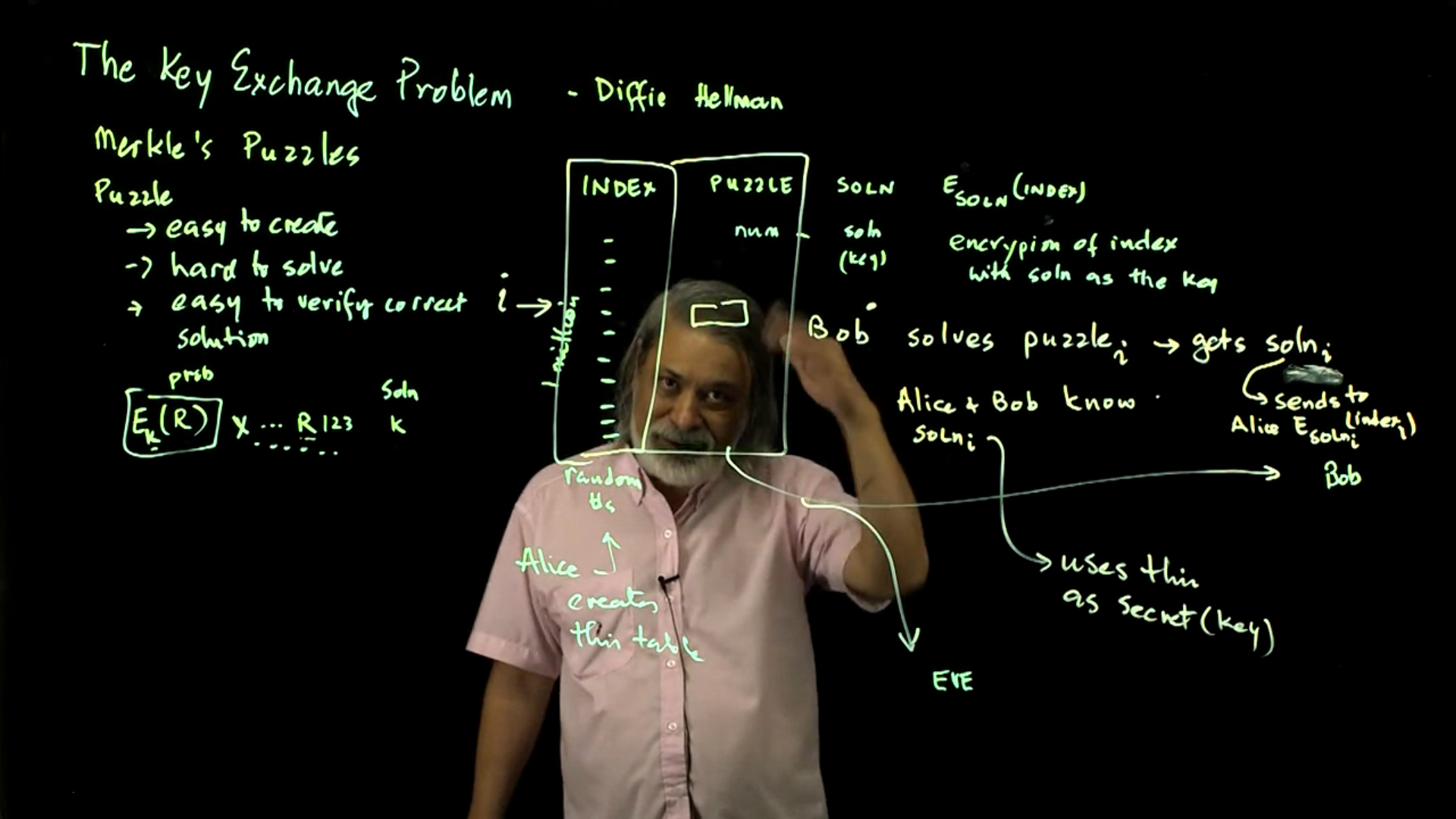
The Key Exchange Problem: This lecture describes the key exchange problem and why Whitfield Diffie (and others) thought it was not possible to solve. The first known solution for the key exchange problem was probably from Ralph Merkle, whose puzzles provide an intriguing solution.
Video 03: The Key Exchange Problem
Section 3: Diffie-Hellman Key Exchange
Diffie-Hellman Key Exchange
The Diffie-Hellman Key Exchange is recognized as the first key exchange protocol. An icon, today it is used for key exchange when using the Elliptic Curve (ECC) public key system. Material in this section of the course introduces Diffie-Hellman and ECC.
Lecture Video Guide
The Diffie-Hellman Algorithm: In spite of Merkle’s solution, it is well accepted in the cryptography community that the Diffie-Hellman algorithm is the first (and proper) key exchange algorithm. This lecture introduces the algorithm and how it works.
Diffie Hellman - continued: This lecture delves into the number theoretic details of Diffie Helman, including generators, finite fields and discrete logarithms. The lecture shows how and why the Diffie-Helman algorithm works.
Elliptic Curve Cryptography (ECC) Algorithm: Elliptic Curve Cryptography (ECC) is a radically different method of constructing public key encryption. Instead of integers (as in RSA), ECC uses points on a cubic curve. This lecture introduces the ECC algorithm, and explores the usage of ECC in Diffie Helman key exchange (ECC-DH), which is gaining popularity in today’s web servers.
Video 04: The Diffie Hellman Algorithm
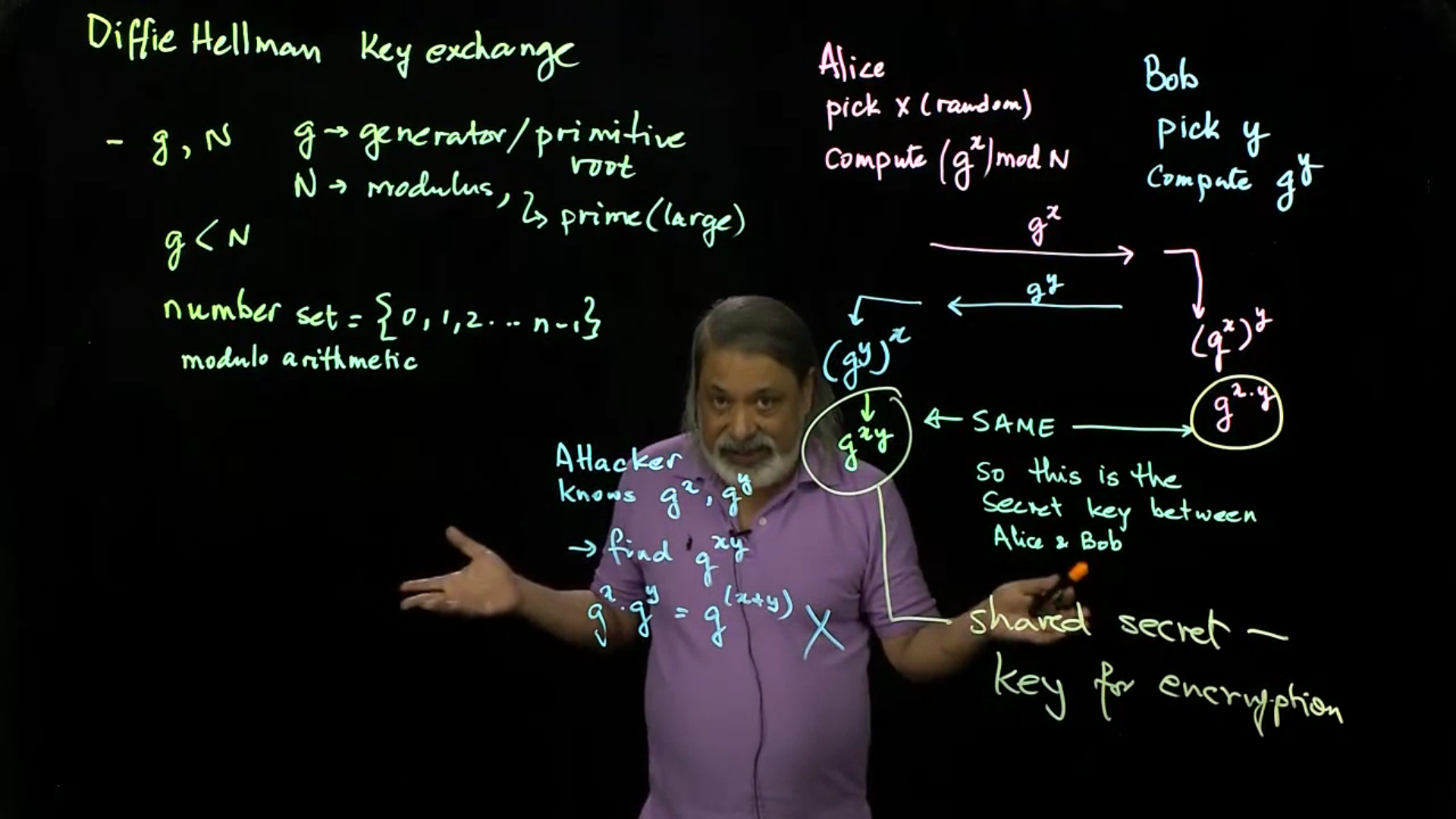
Video 05: Diffie Helman - continued

- notice that authentication is not being provided
Video 06: Elliptic Curve Cryptography (ECC) Algorithm
???
Section 4: Public Keys and Applications
Public Keys and Applications
Public key systems are used to perform a large number of functions in cryptosystems. They are used for authentication, key exchange, signatures and certificates. They also are prone to the famous MITM attack.
Lecture Video Guide
Public Key Encryption: Beginning with a recap on the RSA algorithm, this lecture goes on to show how RSA is used for authentication, key exchange, and secret messaging, and sets the stage for its use in digital signatures and certificates.
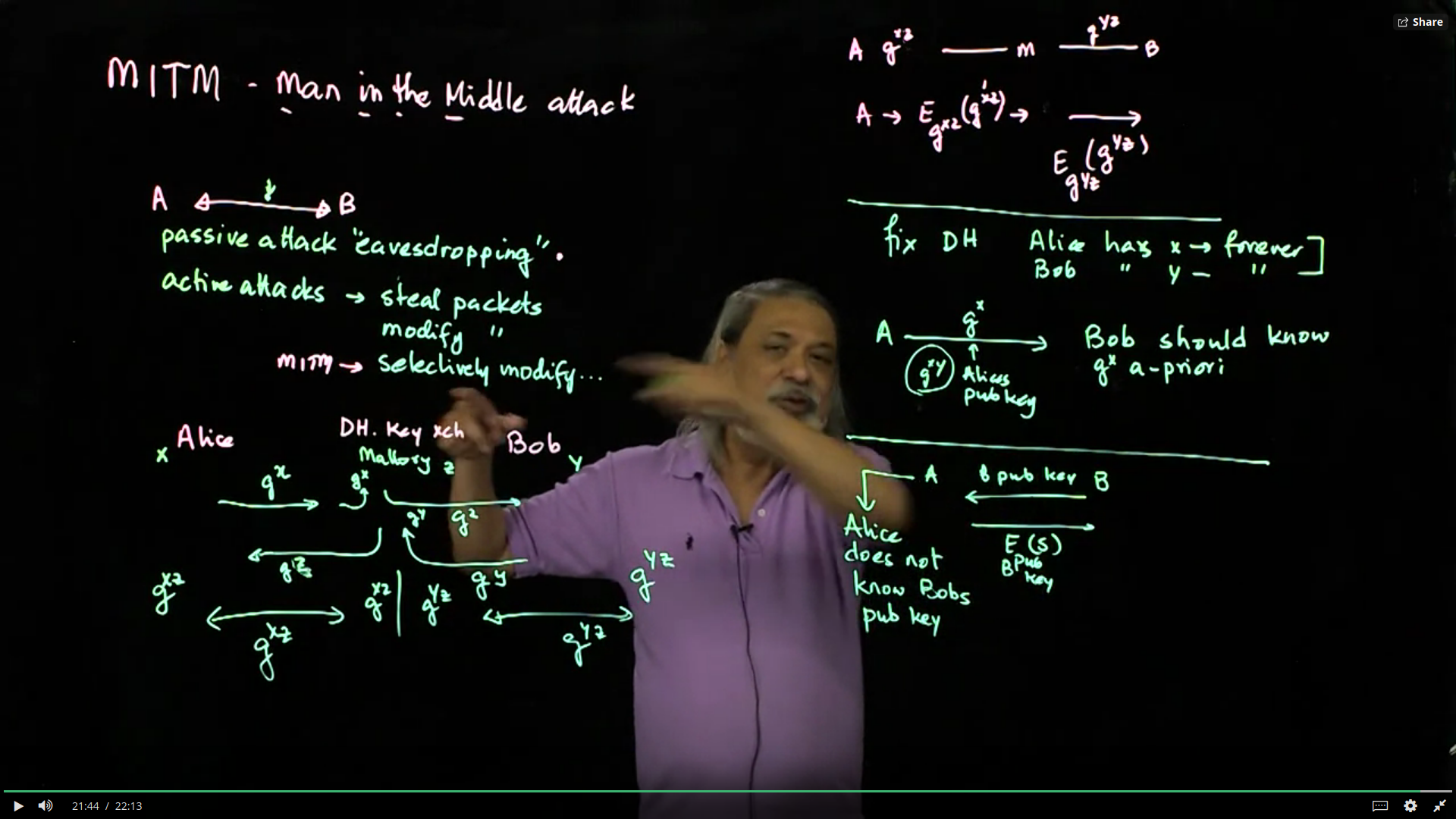
MITM Attacks: All public keys systems suffer from Man-in-the-Middle (MITM) attacks. This lecture discusses the nature of MITM attacks and why they are difficult to prevent.
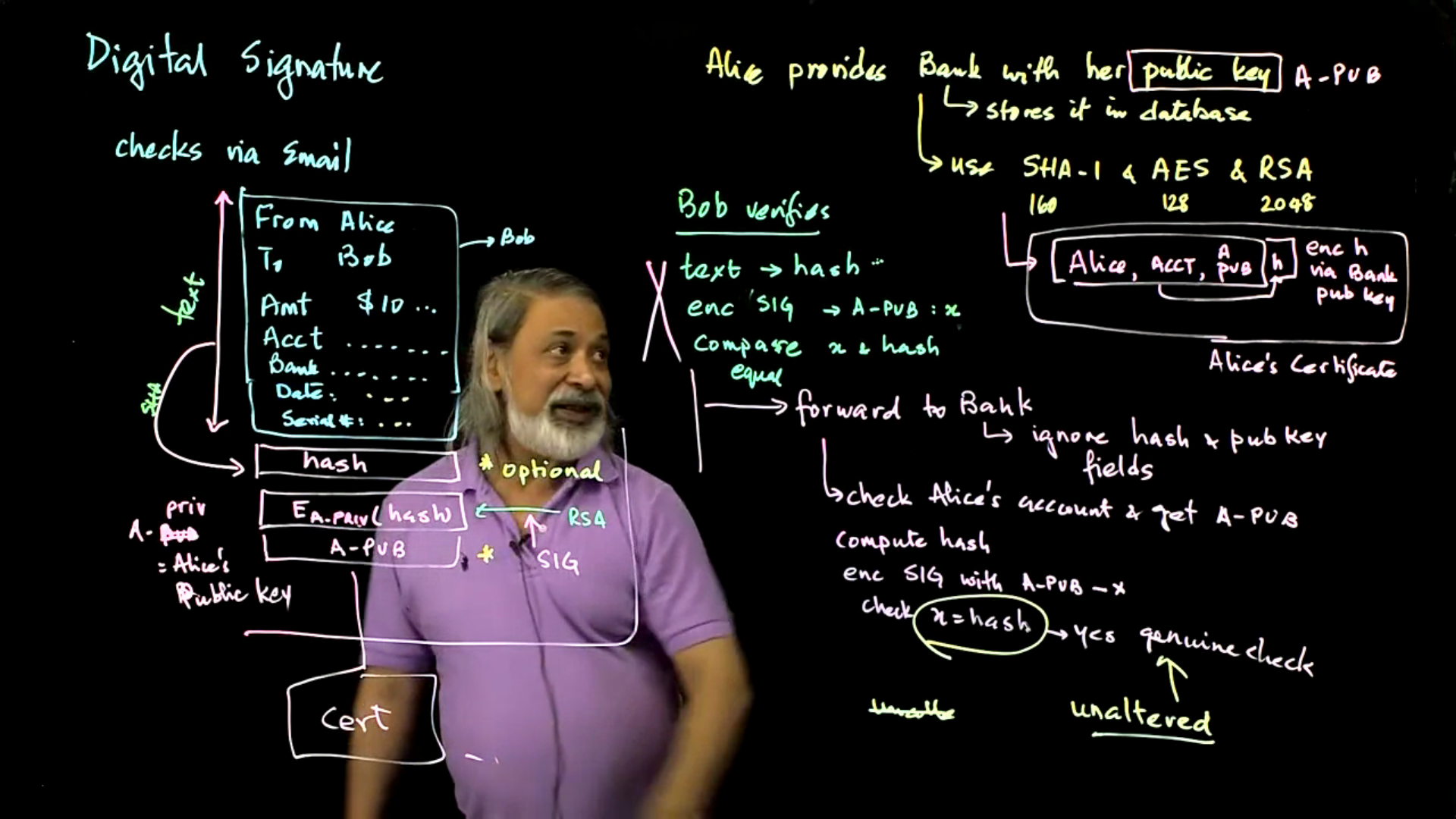
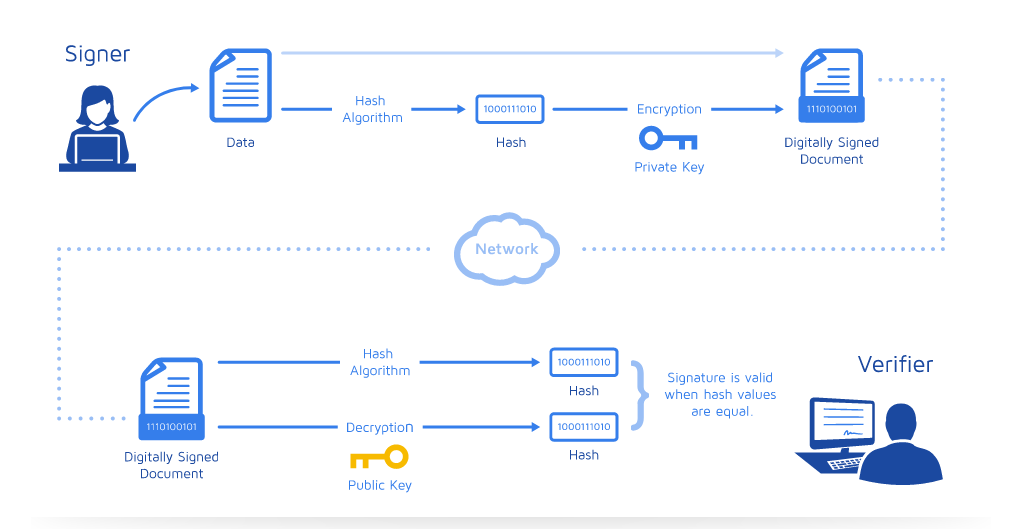
Digital Signatures and Digital Certificates: Digital signatures and certificates are used for authentication, integrity management and resilience to MITM attacks. This lecture presents the definition and the implementation of digital signatures and certificates.
Video 07: Public Key Encryption
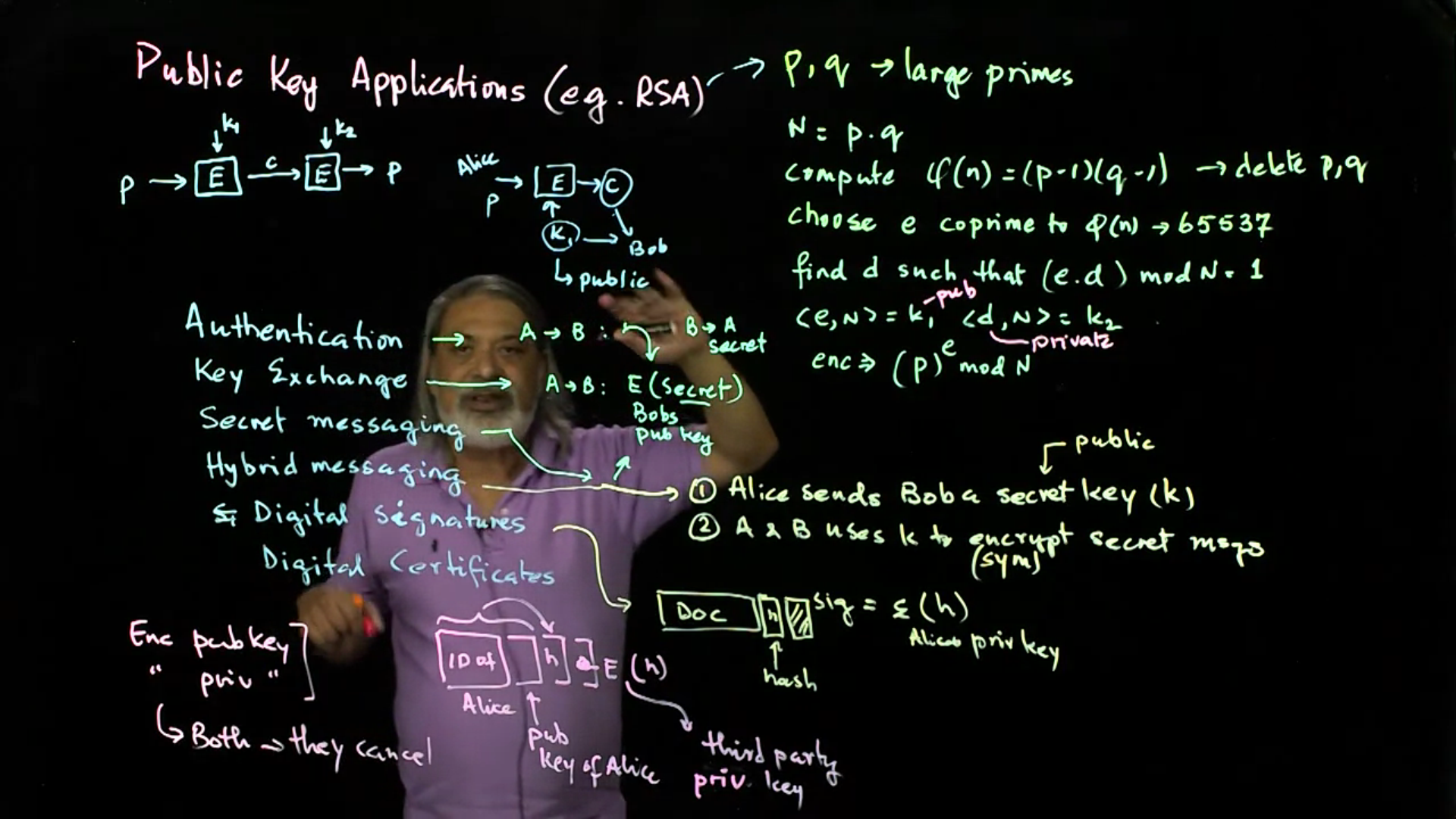
Video 08: MITM Attacks
Video 09: Digital Signatures and Digital Certificates