Week 5 — Cryptographic Protocols, Building Blocks, and Concepts
Contents:
Week 5 Live Event Section 1: Cryptographic Protocols ---- Video 01: Cryptographic Protocols Section 2: Secret / Secure Messaging ---- Video 02: Secret Messaging Section 3: Kerberos (case study) ---- Video 03: The Kerberos Protocol Section 4: Public Key Infrastructure (PKI) ---- Video 04: Digital Signatures and Certificates ---- Video 05: Certificate Authorities (CA) Section 5: Case Study: Secure Sockets Layer (SSL, or TLS) ---- Video 06: Certificates on the Web ---- Video 07: The TLS/SSL Protocol ---- Video 08: SSL Continued
Week 5 Live Event

This week begins with an introduction to cryptographic protocols and secret messaging, and goes on to present the Kerberos authentication protocol as a case study, followed by a deeper dive into the PKI systems, certificate authorities, and a detailed look at how the HTTPS protocol (also known as SSL or TLS) works.
Topic Outline:
- Cryptographic Protocols
- Secret Messaging
- Case Study: Kerberos
- Public Key Infrastructure (PKI)
- Case Study: Secure Sockets Layer (SSL or TLS)
Cryptographic Protocols
This lecture depicts the subtleties and properties of cryptographic protocols. Cryptographic protocols are self-enforcing, multi-party, step-by-step protocols that do not rely on mutual trust. They are often complex and fragile, with properties such as privacy and non-repudiation. In this lecture, we outlines the goals and properties of such protocols.
Section 1: Cryptographic Protocols
Video 01: Cryptographic Protocols
What is a cryptographic protocol? A step-by-step procedure to accomplish a goal using cryptographic methods.
- Describes how the cryptographic algorithms should be used.
- Allows for multi-party with no mutual trust.
- Often complex and fragile.
What is the difference between a protocol and an algorithm?
They are the same, but the term protocol is prefered because computation is done across multiple parties (similar to networking).
Notes:
- Verification of cryptographic protocols is not possible.
- “Do not role your own crypto”. However, you may use the basic building blocks of cryptography to create your own protocol (but beforehand, see if what you want has already been done).
What are their properties?
- Privacy – encryption
- Integrity – no malicious modification
- Authentication – ID verification (needs to be done at every step in your protocol)
- Non-repudiation – i.e., you cannot take back what was done by you
- Access control
Note: They are not really independent, often they need to be together.
Types of protocols (these terms come from more from law rather than CS):
- Arbitrated
- happen during the fact
- requires a third party
- example: escrew
- Adjudicated
- after the fact (like a judge)
- Self Enforcing
- goal of crypto
Section 2: Secret / Secure Messaging
Video 02: Secret Messaging
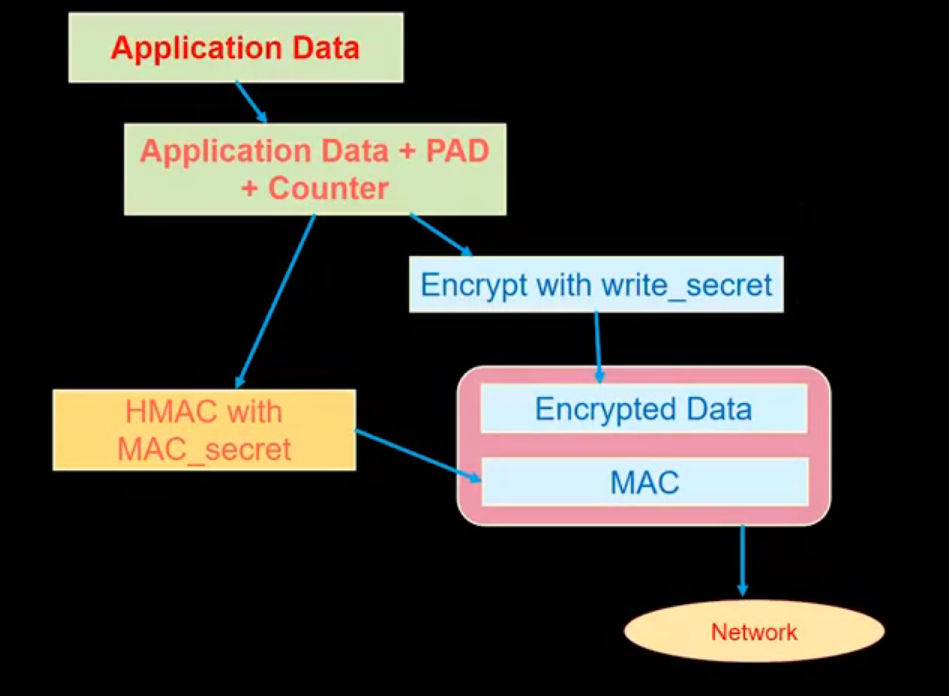
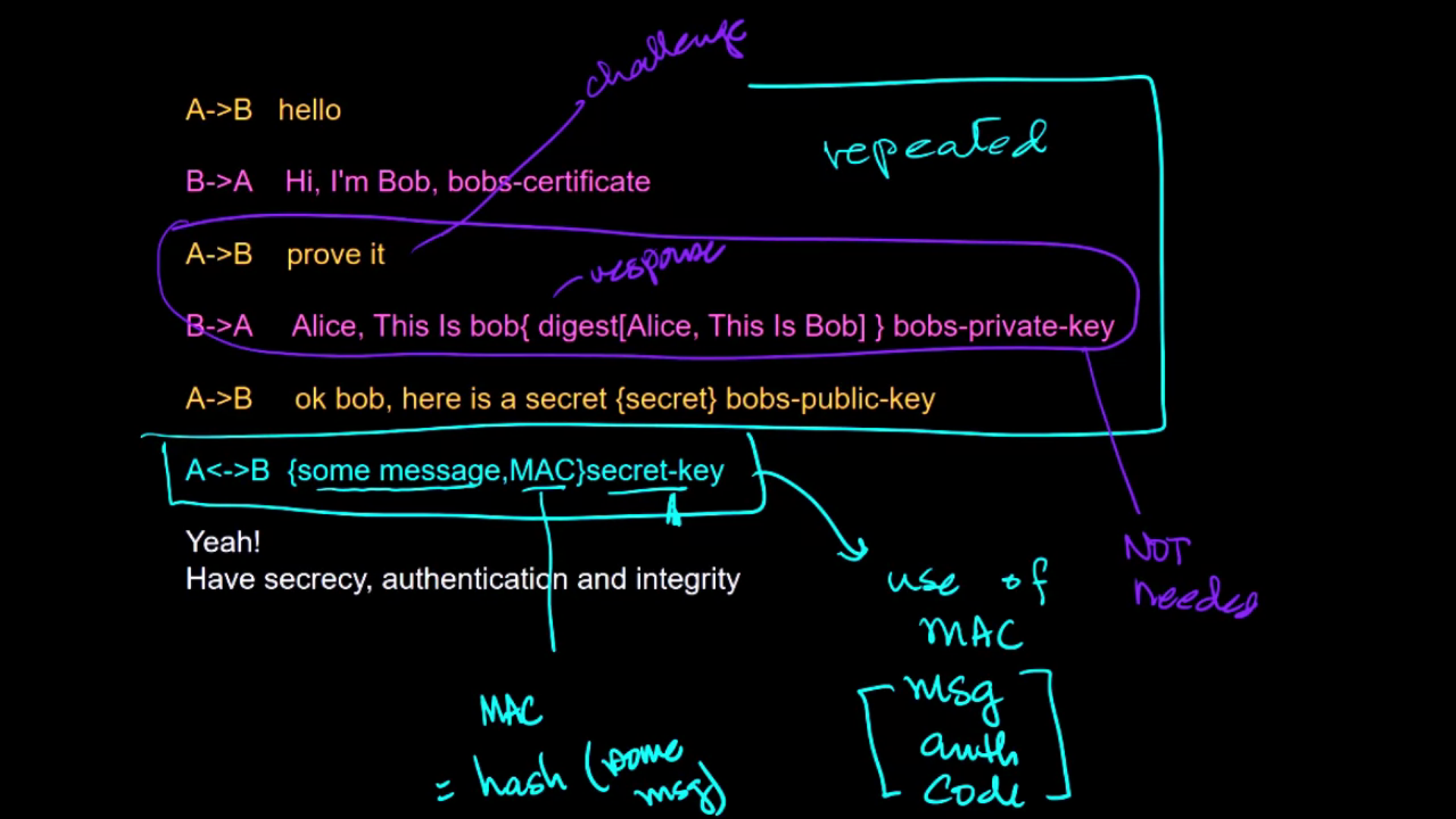
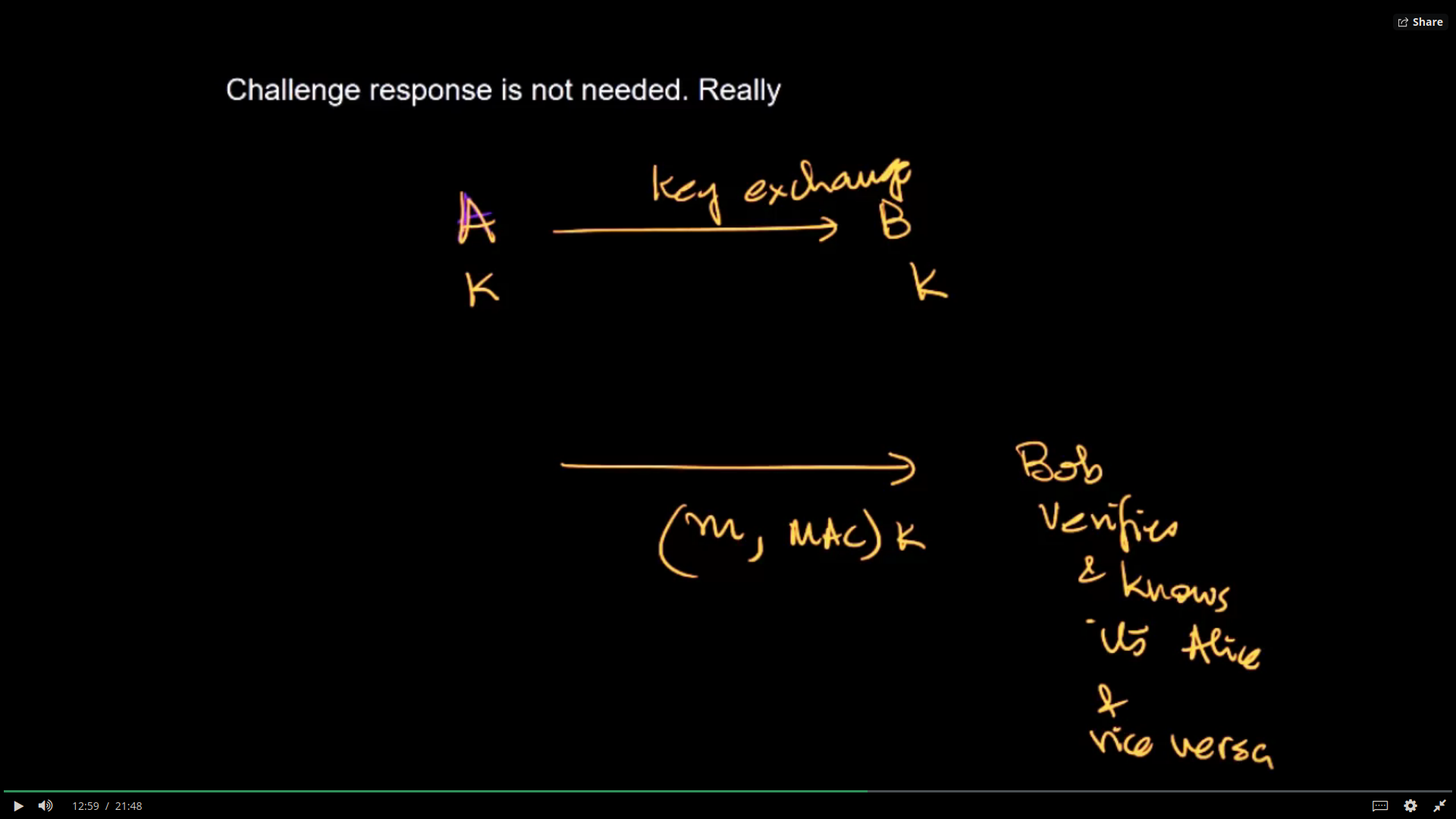
Sending messages that are private, authentic, and non-tamperable is called secret (or secure) messaging. Sending messages that are secret is harder than you might think. Every message must be authenticated, encrypted, tamper-detectable and free from MITM attacks. Combinations of public-key and symmetric key encryption along with message authentication codes (MAC) are used to do secret messaging.
MAC == Message Authentication Codes
To avoid message tampering:
- Compute hash and concatenate.
- Encrypt.
- Send.
What about authentication?
- Messages need to be encrypted / decrypted using a symmetric key (R).
Notes:
- Message hash can be concatenated without encryption, but this is not good practice.
- A bad way of doing it is first encrypting the message, then computing a hash of the encrypted message, concatenate and send.
- this is like parity, completely insecure.
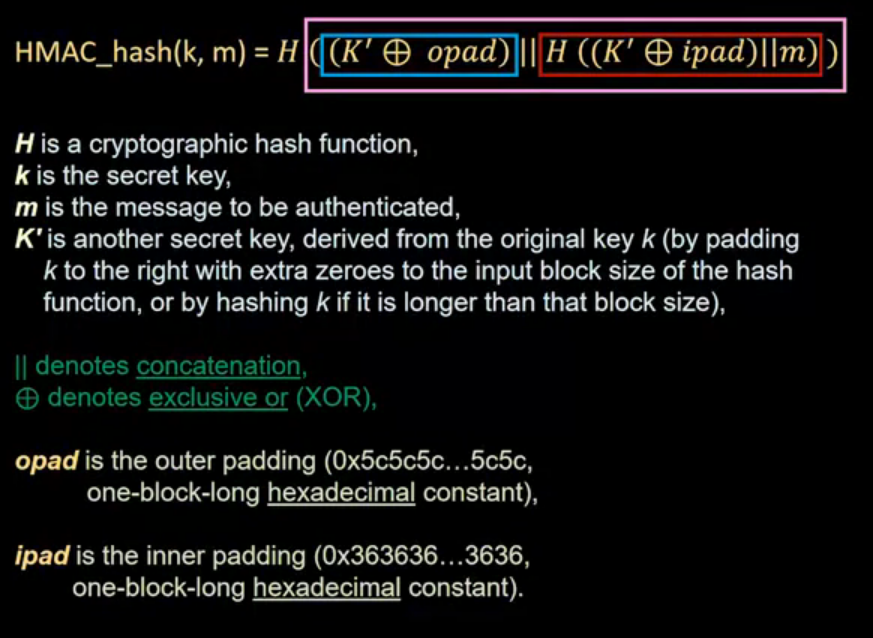
The standard algorithm used is HMAC (hash MAC / Keyed MAC).
Why is it used?
Because of the length extension atack on hash functions (similar to birthday attcks).
“In cryptography and computer security, a length extension attack is a type of attack where an attacker can use Hash(message1) and the length of message1 to calculate Hash(message1 ‖ message2) for an attacker-controlled message2, without needing to know the content of message1. Algorithms like MD5, SHA-1, and SHA-2 that are based on the Merkle–Damgård construction are susceptible to this kind of attack. The SHA-3 algorithm is not susceptible.”
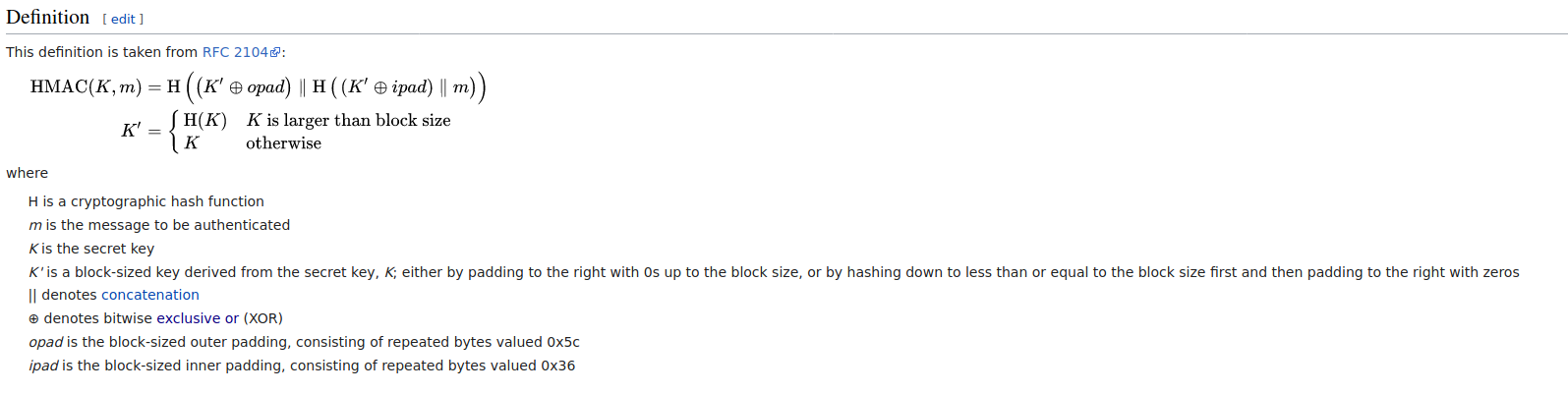
Remark:
- opad = 0x5c5c
- ipad = 0x3636
Section 3: Kerberos (case study)
Video 03: The Kerberos Protocol
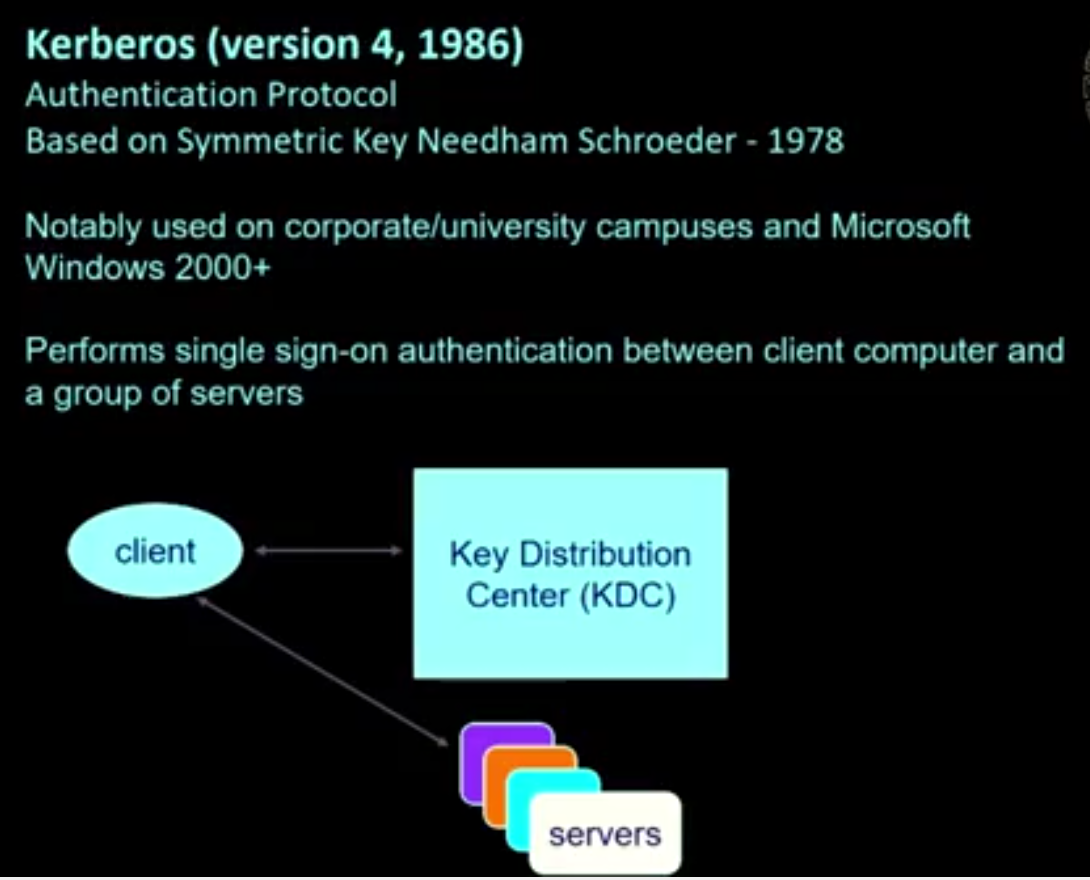
The Kerberos protocol is an authentication protocol that was the precursor to the current single sign-on systems. It was developed in 1986 from a symmetric key version of Needham and Schroder. This lecture discusses the details of Kerberos and how good cryptographic designs are done. The Kerberos case study provides a strong learning opportunity, particularly in regards to the nuances of cryptographic protocols.
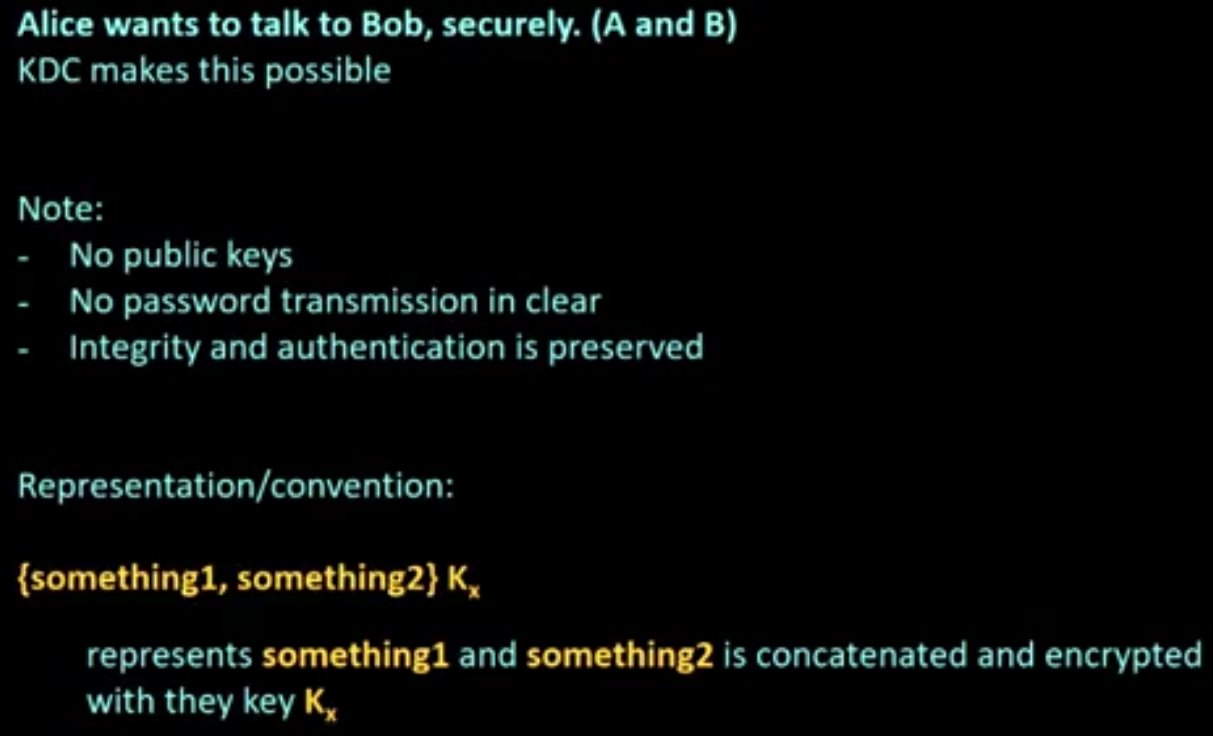
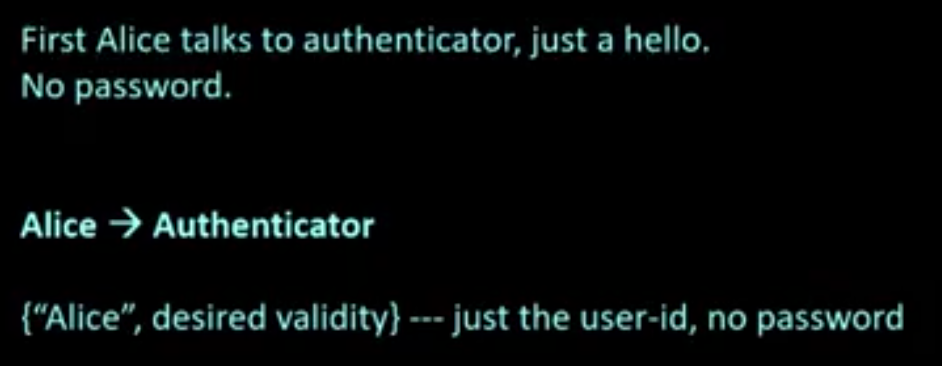
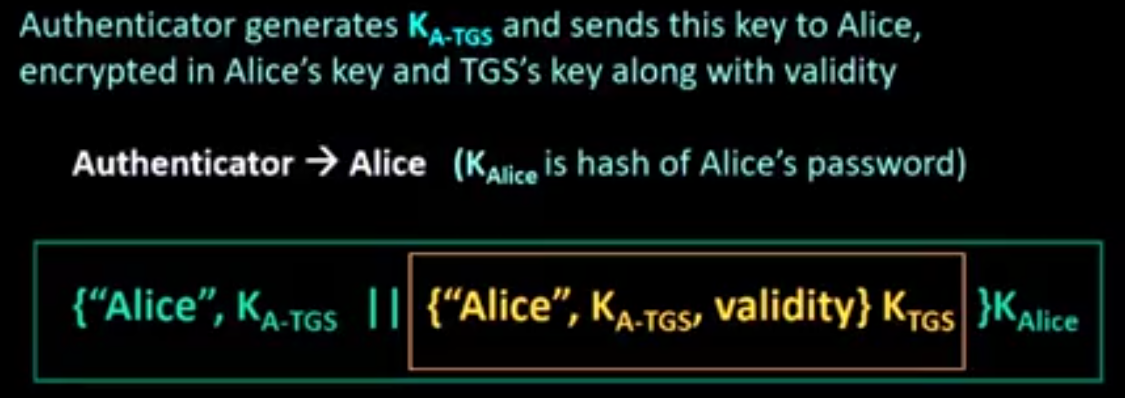
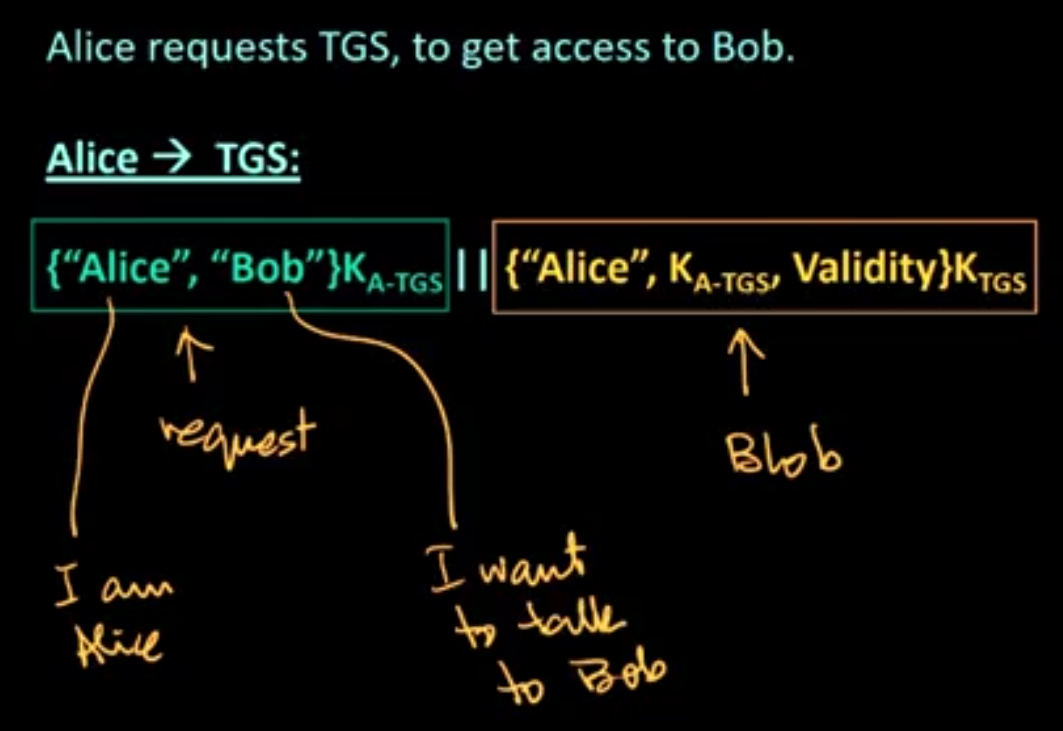
Kerberos:
Kerberos is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner.
Its designers aimed it primarily at a client–server model and it provides mutual authentication—both the user and the server verify each other’s identity.
Kerberos protocol messages are protected against eavesdropping and replay attacks.
Kerberos builds on symmetric key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of authentication.
Kerberos uses UDP port 88 by default.
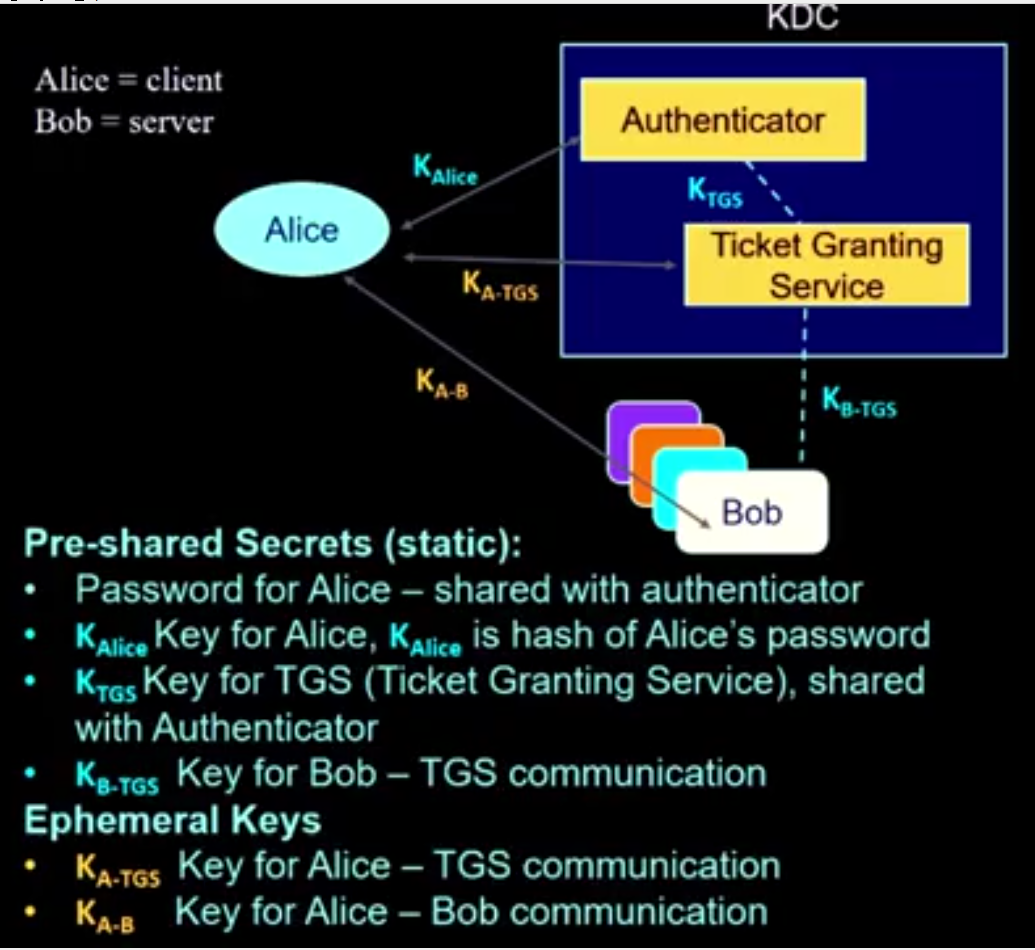
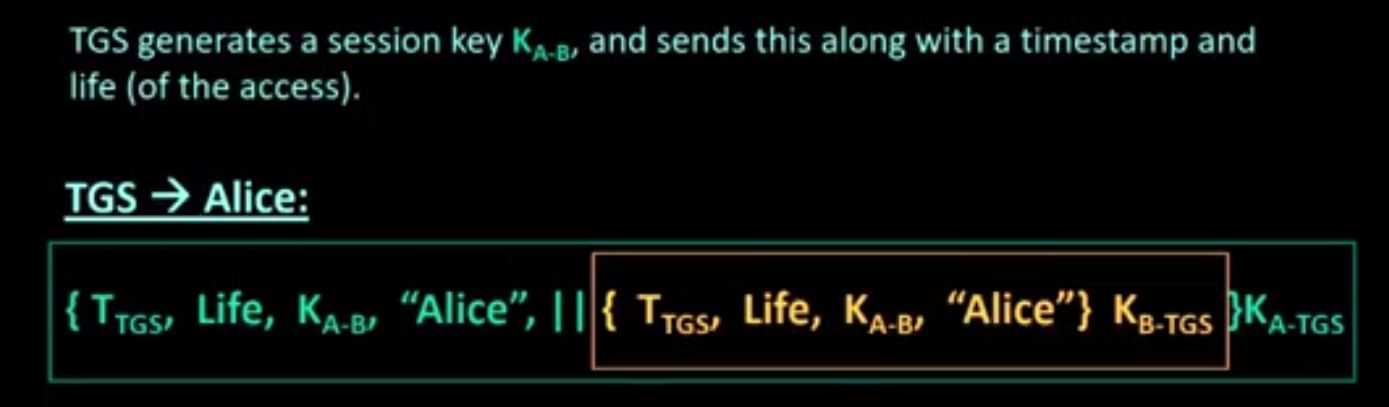
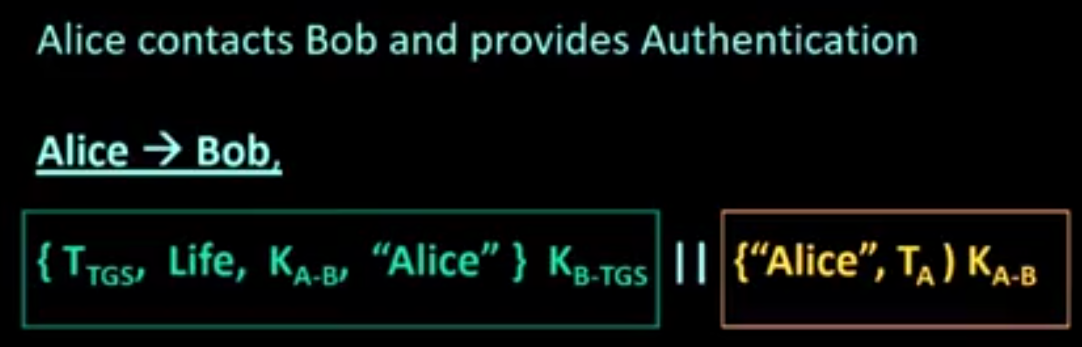
Several steps:
- sort of complex
- can seem confusing
- several things (i.e., contents of messages) look unnecessary, but is needed
- think secrecy, authentication, integrity


Section 4: Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) is the fabric that holds together trust management in the world wide web. Certificates and certificate authorities act as the pillars of this technology.
Lecture Video Guide
Digital Signatures and Certificates: This lecture takes a closer look at digital signatures and certificates and discusses the properties and rules of signing digital documents.
Certificate Authorities (CA): Digital certificates are issued by trusted agencies called Certificate Authorities (CA). Root Certificate Authorities function as the root of trust. Web of Trust is a decentralized system for managing trust. Trust management helps ensure correct authentication and acts as a deterrent to MITM attacks. This lecture explores Certificate Authorities and surrounding topics.
Video 04: Digital Signatures and Certificates
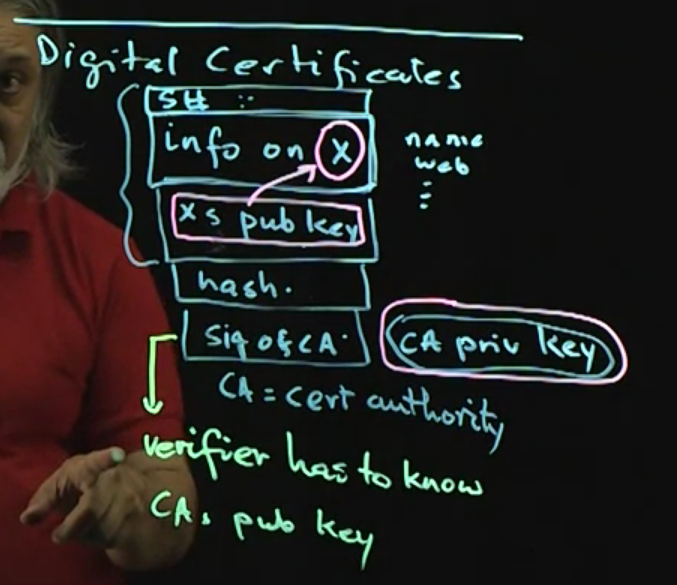
How do digital signatures work?
- write a document
- compute hash
- encrypt hash using your private key
How to verify?
- receive a document
- compute hash
- decrypt received hash/signature using originator public key
- if both computed and decrypted hash match then the document is valid
Properties of digital signatures:
- authentic
- not forgeable
- not alterable (document)
- not reusable
- not repudiable
Rule for digital signatures: Do not sign anything you did not create.
Then what should you do?
- create the document yourself
- alter / perturb the document
Why?
- so that you dont sign a hash for a different document
What is the primary usage of digital signatures?
- digital certificates
Video 05: Certificate Authorities (CA)
PKI components:
- signitaures
- certificates
- trust management
- centralized – CA
- decentralized / distributed – web of trust
Remarks:
- lots of public keys are already embeded in your browser / OS
- these are called a keystore / root of trust
- the people who run the network, should not have the authority to install their own certificates onto their users computers

- there can be hierarchical CAs
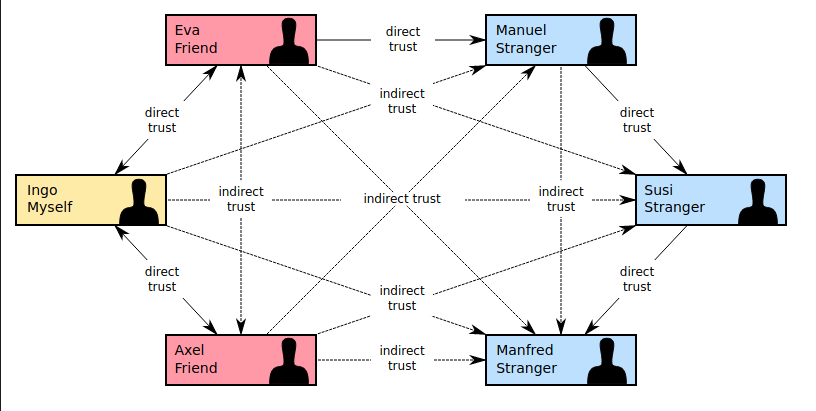
What is the web of trust?
Revocation of certificates?
OCSP (Online Certificate Status Protocol):
- Alice and Bob have public key certificates issued by Carol, the certificate authority (CA).
- Alice wishes to perform a transaction with Bob and sends him her public key certificate.
- Bob, concerned that Alice’s private key may have been compromised, creates an ‘OCSP request’ that contains Alice’s certificate serial number and sends it to Carol.
- Carol’s OCSP responder reads the certificate serial number from Bob’s request. The OCSP responder uses the certificate serial number to look up the revocation status of Alice’s certificate. The OCSP responder looks in a CA database that Carol maintains. In this scenario, Carol’s CA database is the only trusted location where a compromise to Alice’s certificate would be recorded.
- Carol’s OCSP responder confirms that Alice’s certificate is still OK, and returns a signed, successful ‘OCSP response’ to Bob.
- Bob cryptographically verifies Carol’s signed response. Bob has stored Carol’s public key sometime before this transaction. Bob uses Carol’s public key to verify Carol’s response.
- Bob completes the transaction with Alice.
Remark: it is not on by default.
Section 5: Case Study: Secure Sockets Layer (SSL, or TLS)
Using the PKI infrastructure described before, we show how secure messaging (HTTPS) works with web browsers and servers.
Lecture Video Guide
Certificates on the Web: All secure web servers use certificates. This lecture shows how to access certificates, public keys and other information about secure web servers.
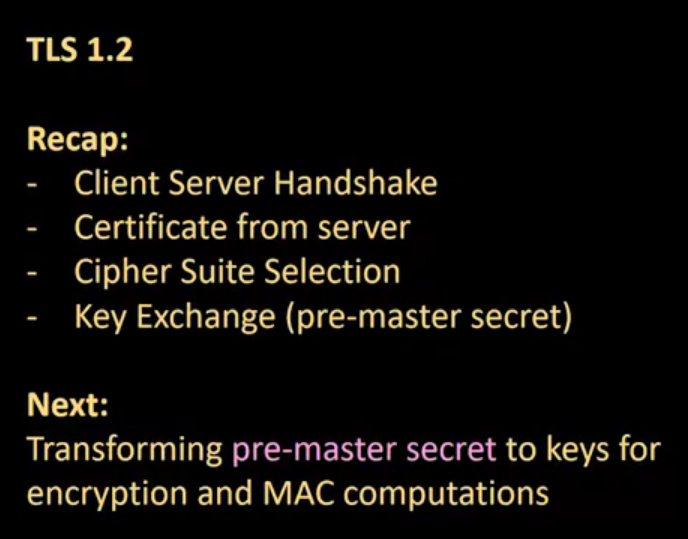
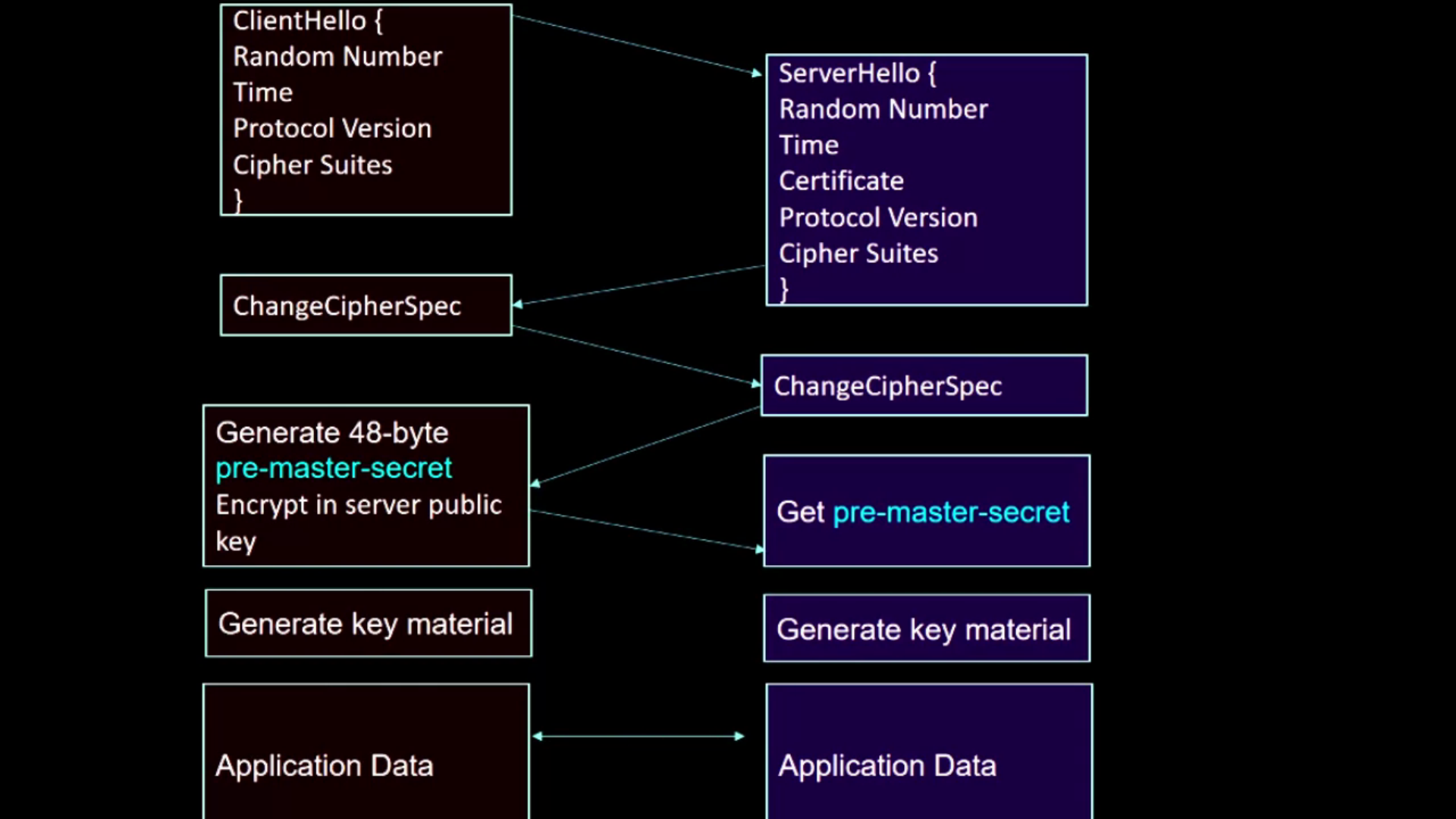
The TLS/SSL Protocol: Secure Sockets Layer (SSL) or Transport Level Security (TLS) is the messaging protocol used in HTTPS connections. This lecture shows the details of the SLL protocol.
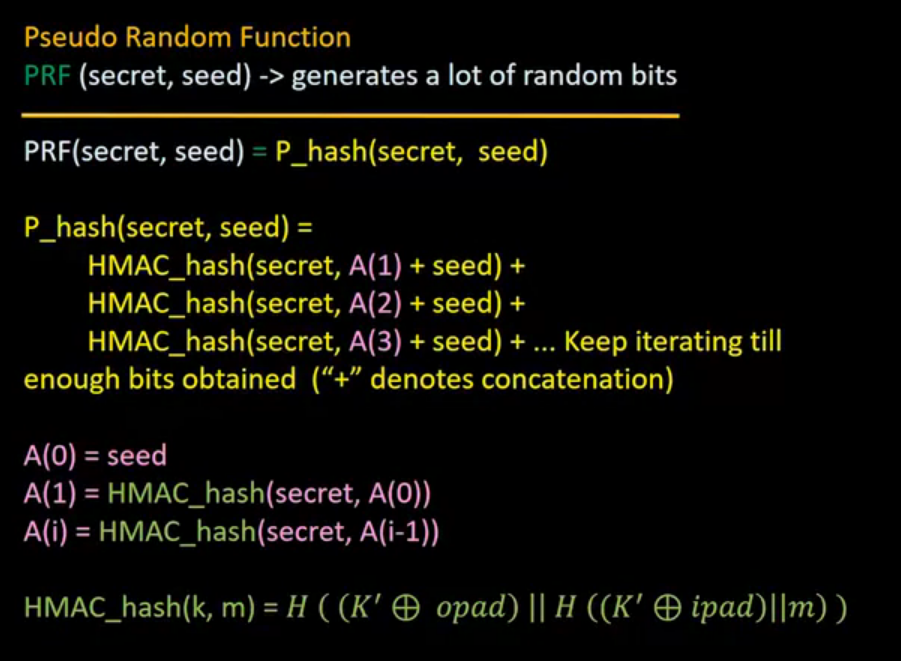
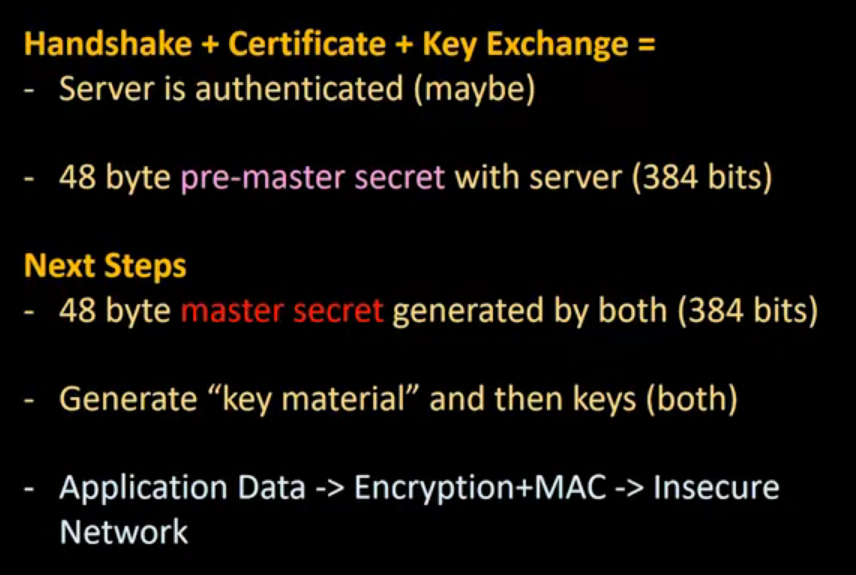
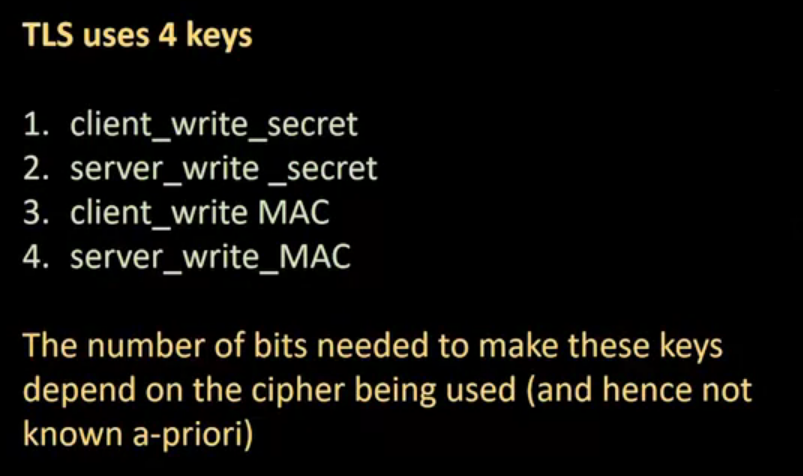
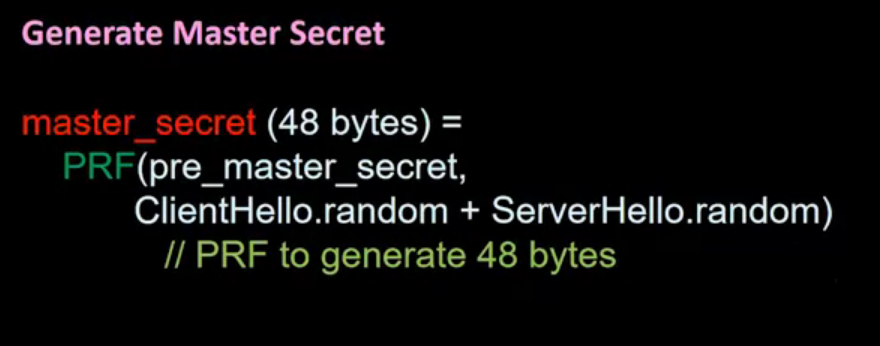
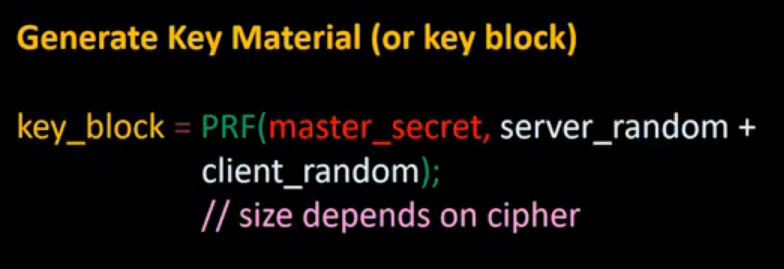
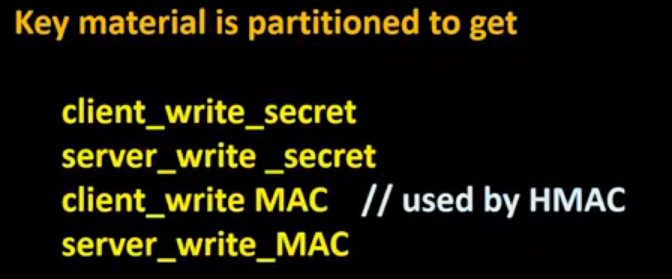
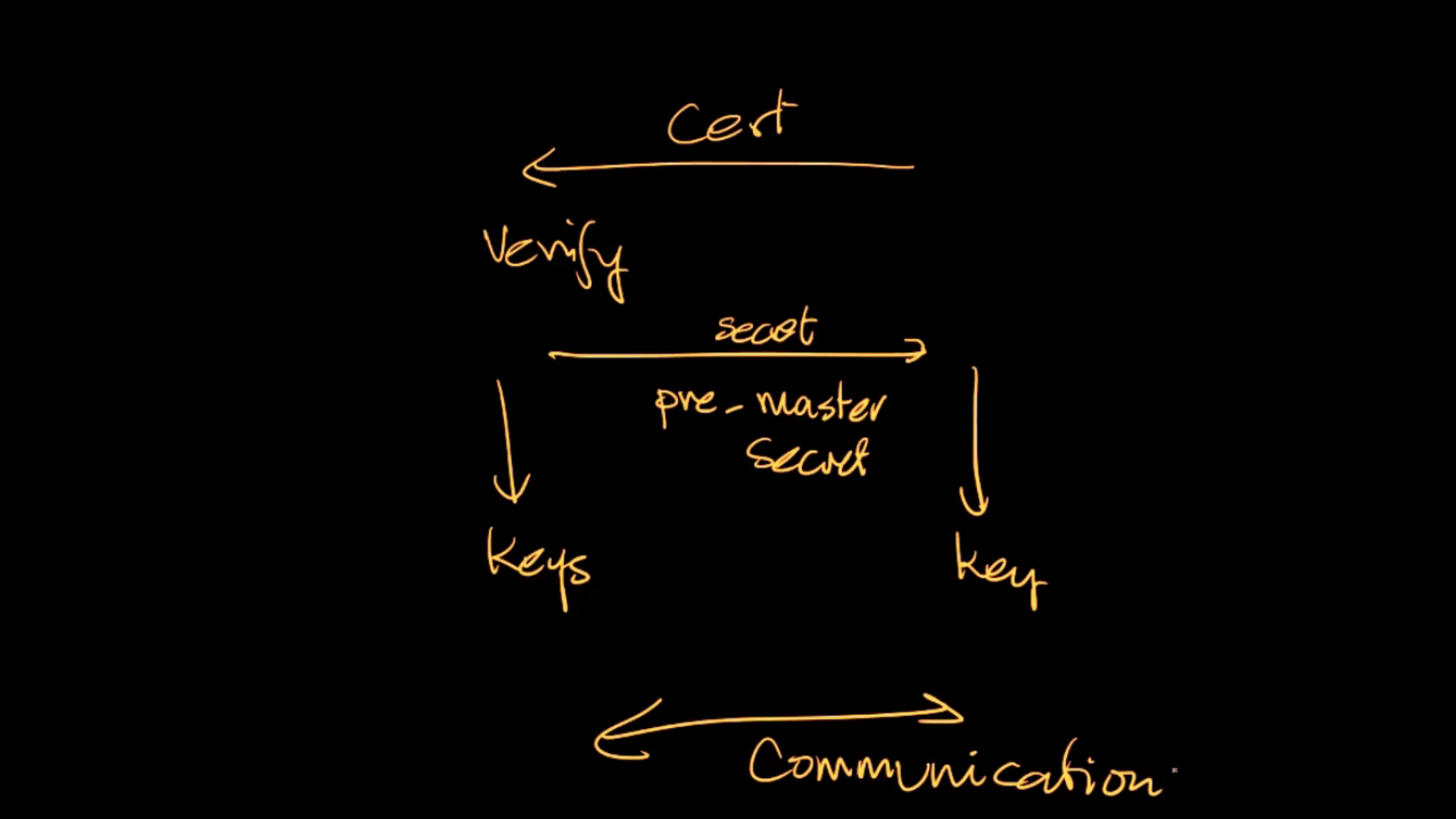
SSL Continued: The inner details of the SSL protocol is presented in this lecture, including the pre-master secret, how to generate a master secret and key material, and PRF and HMAC functions.
Video 06: Certificates on the Web
Nothing to note here.
Video 07: The TLS/SSL Protocol

Video 08: SSL Continued