Week 8 — Money and Politics
Contents:
Section 1: Cut and Choose ---- Video 01: Blind Signatures ---- Video 02: Anonymous Money Orders ---- Video 03: Graph Isomorphism and Zero Knowledge Proofs ---- Video 04: FFS Proof of Identity ---- Video 05: Oblivious Transfer Section 2: Cryptographic Techniques ---- Video 06: Secret Splitting and Secret Sharing ---- Video 07: Bit Commitment ---- Video 08: Timestamping ---- Video 09: Dining Cryptographers ---- Video 10: Commutative Encryption and Mental Poker
Section 1: Politics and Cryptography
Besides its potential to aid in spying, cryptography can also be coerced to have “backdoors.” In this section, we discuss privacy issues in the current political climate.
Lecture Video Guide
Encryption with Backdoors: Many law enforcement agencies and governments have incentive to spy on users of encrypted communications (all of us), hence the need for encryption with backdoors only accessible by government. Is this possible, or advisable?
Plausible Deniability and Perfect Forward Security: Saying “I did not do it” is a denial. A stronger response is, “Can you prove that I did it, in spite of finding all keys?” If the answer is “no,” I have plausible deniability. That is to say, no traces are found. This entangles with the idea of perfect forward security. This lecture discusses these two important concepts in communications.
MITM attacks and Diffie Hellman: This lecture revisits Diffie Helman and MITM attacks because Diffie Helman has properties that allow for both perfect forward security and plausible deniability. However, MITM is impossible to solve. This lecture shows why, and how can we find solutions to the problem.
The “Off the Record” Protocol: Off the Record (OTR) is an instant messaging protocol that is built into several off-the-shelf messengers, notably signal and pidgin. This lecture presents an overview of the complex inner workings of this protocol.
Secure Elections - Part 1 & 2:
Electronic and digital voting methods are common in elections, though seriously insecure. It is nearly impossible to ensure secure voting protocols. The protocol is covered in this two-part lecture.
Video 01: Encryption with Backdoors

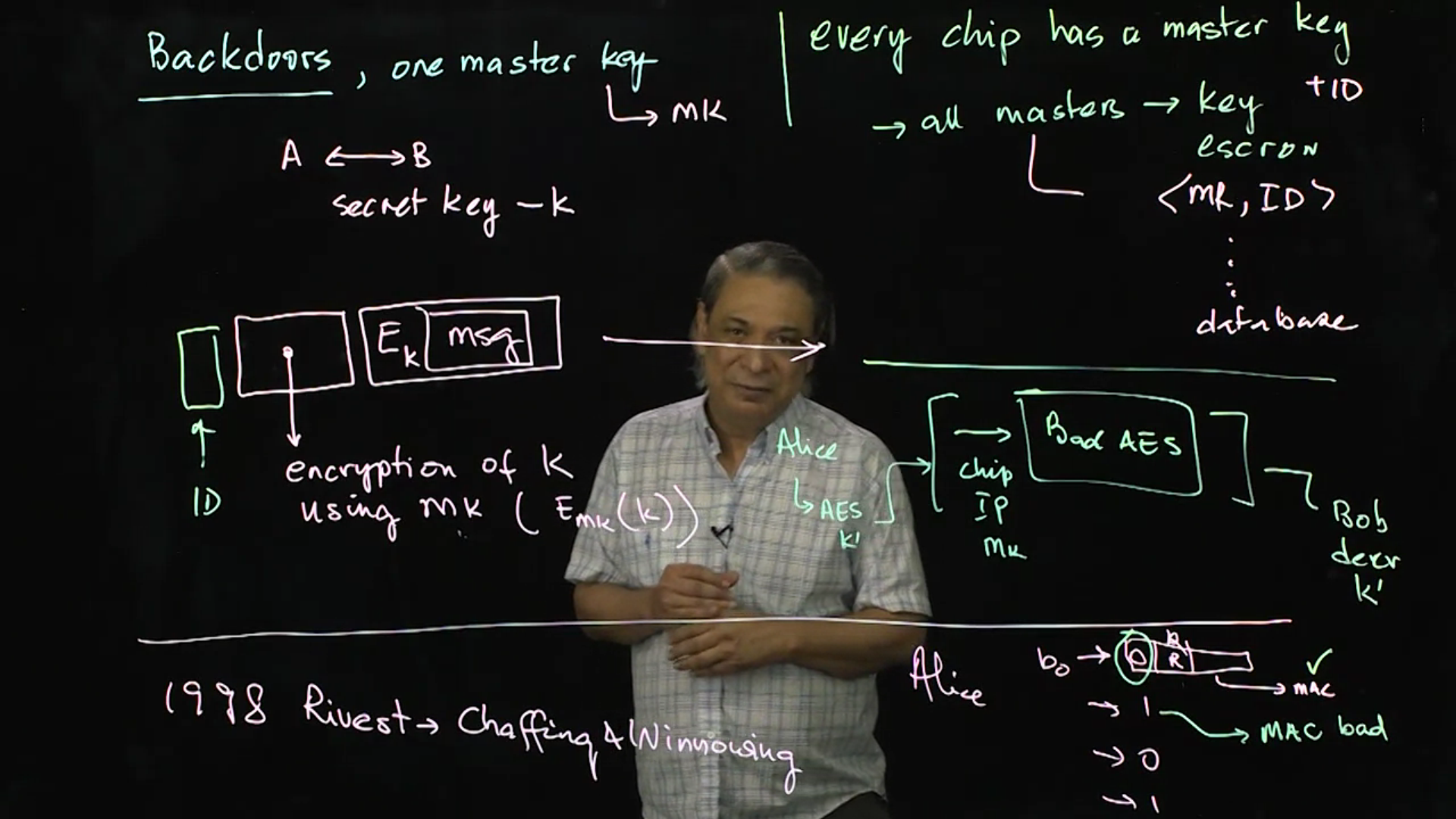
Video 02: Plausible Deniability and Perfect Forward Security

Video 03: MITM attacks and Diffie Hellman
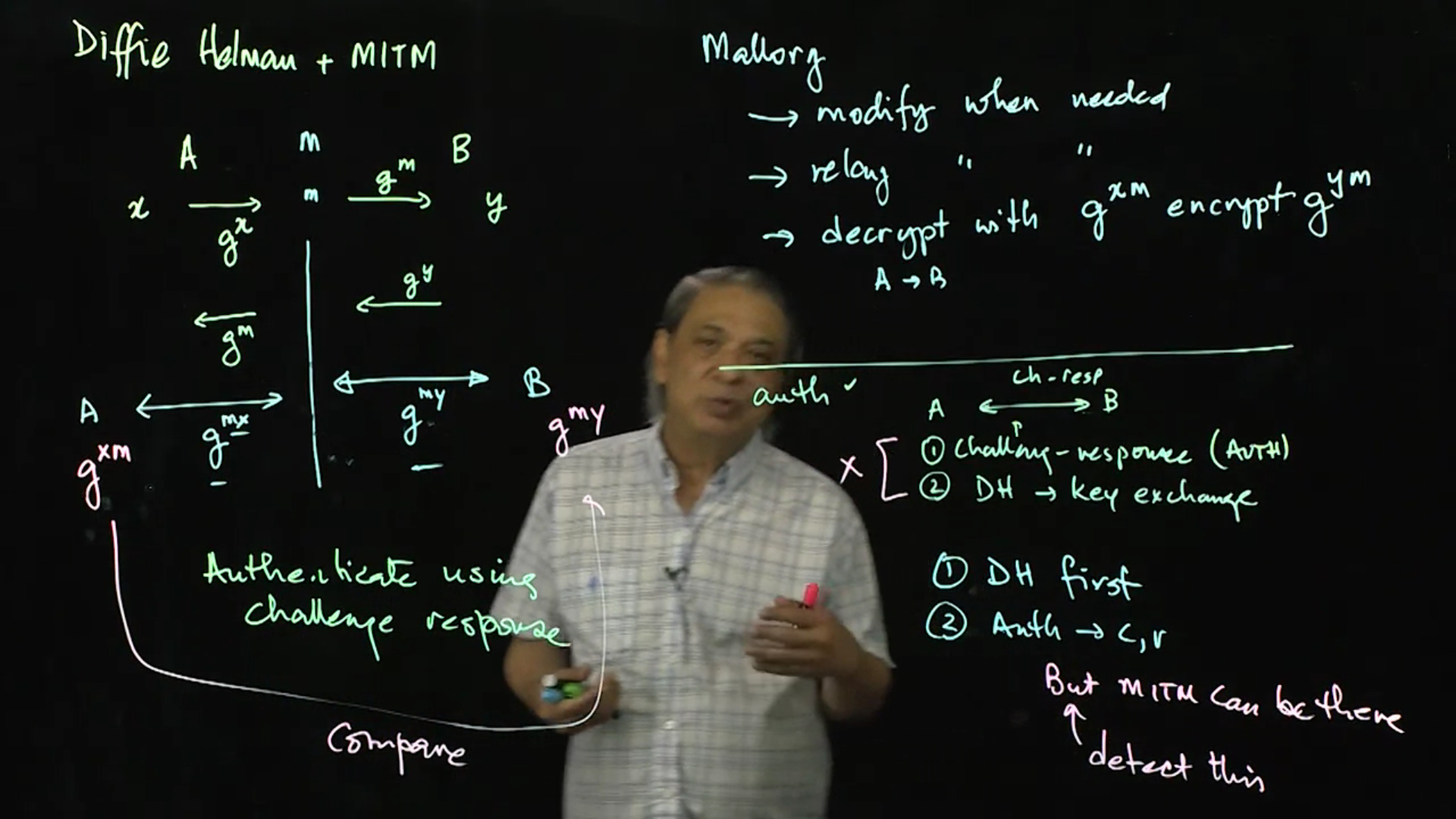
Video 04: The “Off the Record” Protocol

Video 05: Secure Elections - Part 1
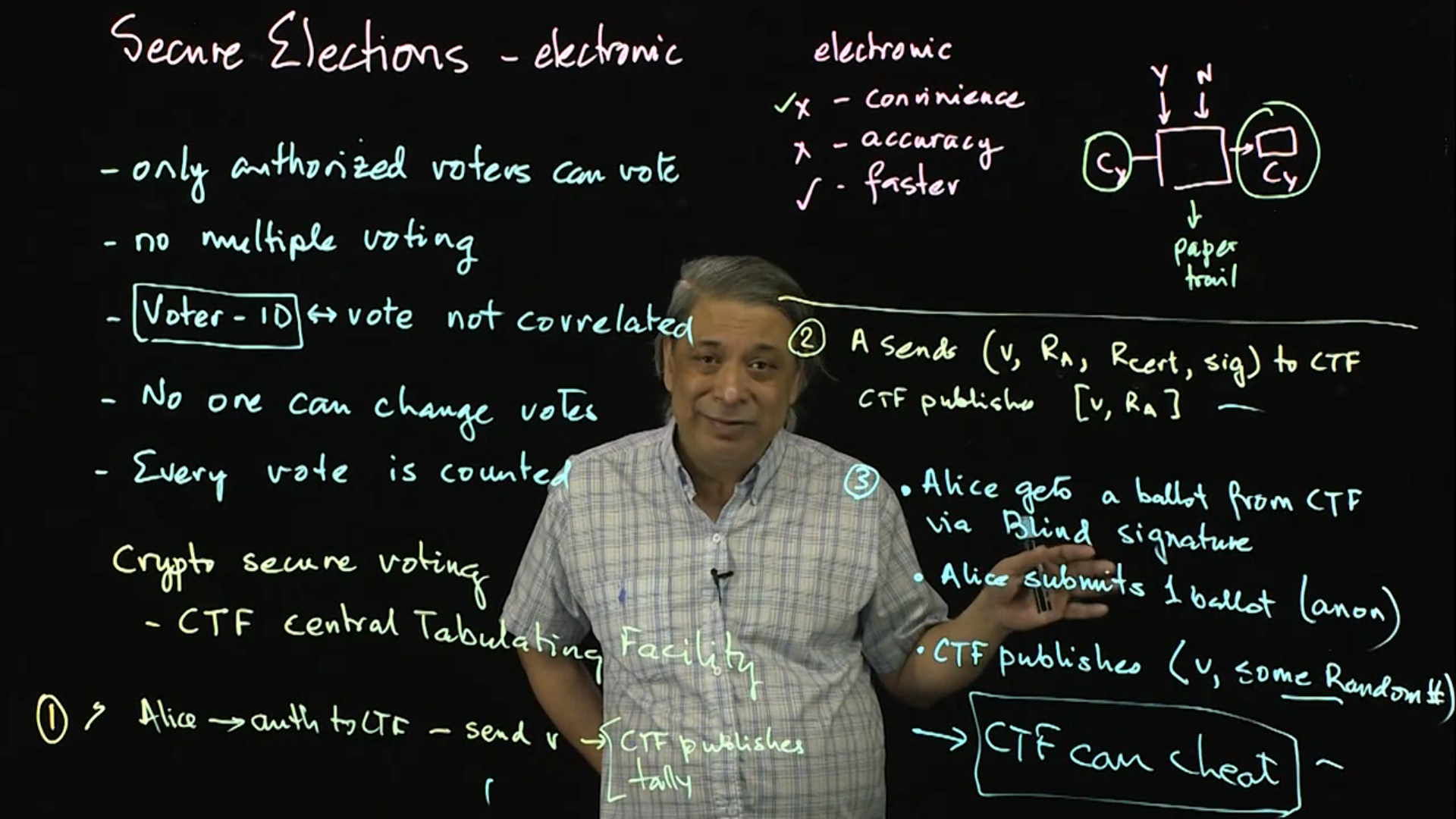
Video 06: Secure Elections - Part 2

Section 2: Cryptocurrency and Digital Cash
Money is often considered a universal language–something that everyone can understand–and is commonplace. People interact with money on a daily basis through trusted banks, and now, with electronic transactions, digital money (currencies), and digital cash (cash-like anonymity). In this section of the course, we discuss how cryptography makes all of this possible.
Lecture Video Guide
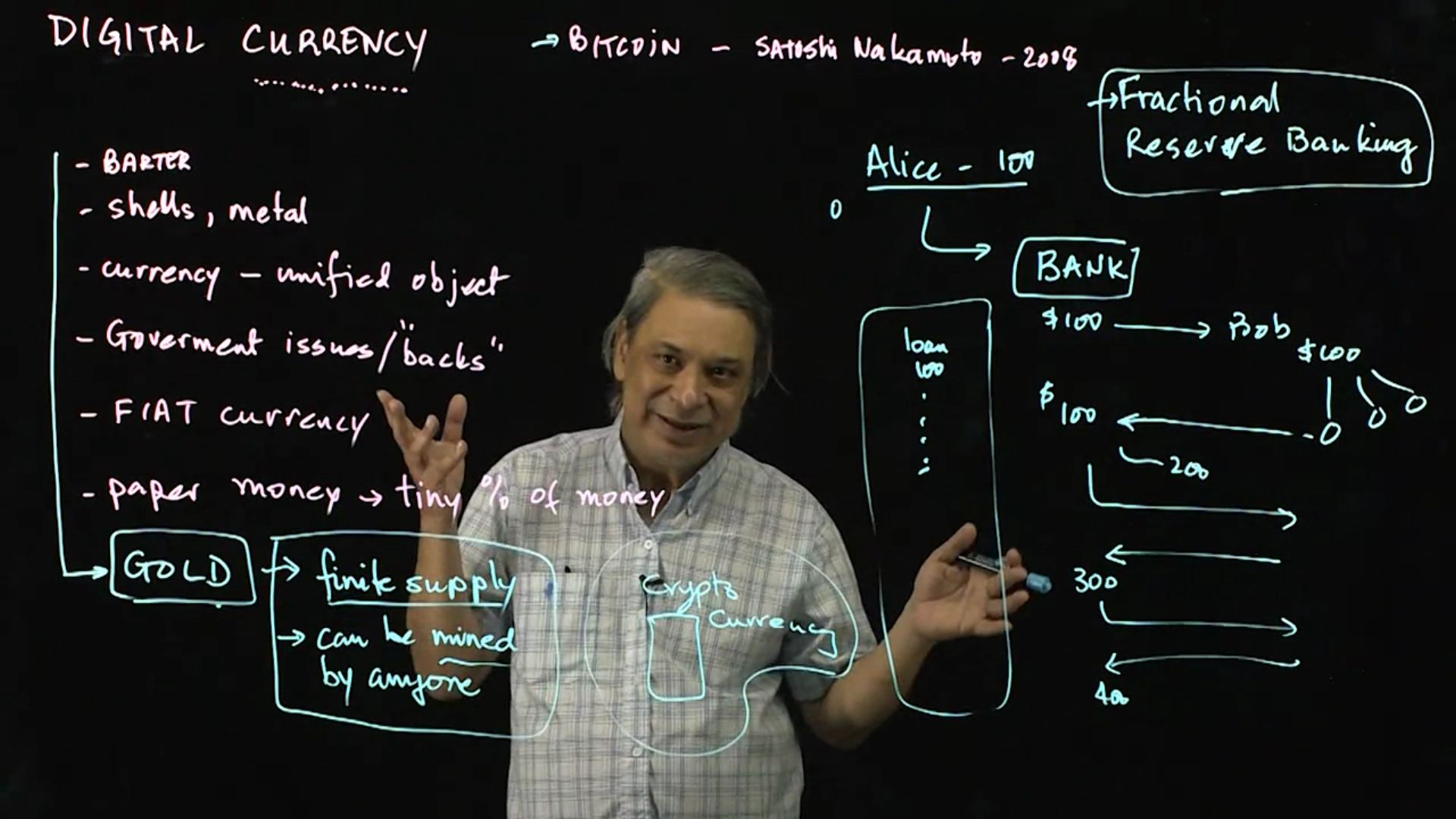
Digital Currency: What is currency? This lecture takes a brief detour from cryptography to lay the foundations for understanding digital currency and how it works.
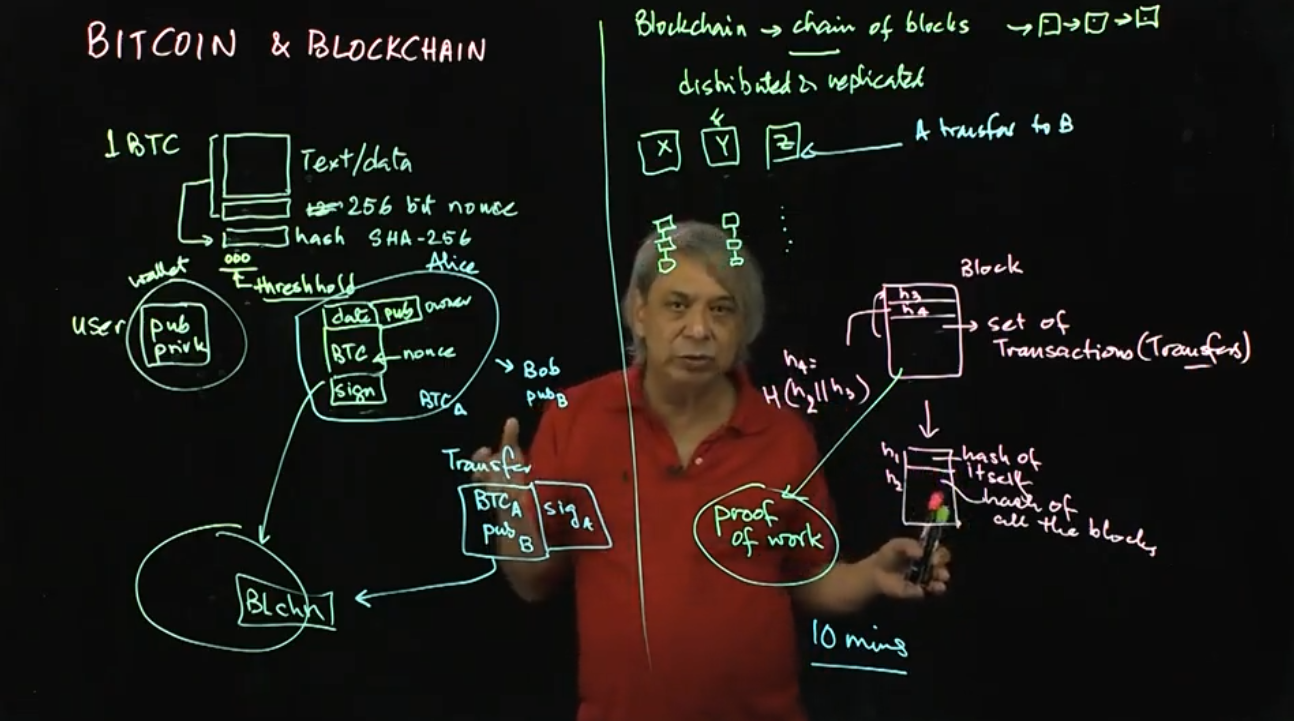
Bitcoin and Blockchain: Bitcoin is one of many digital currencies. Though simple, it requires a blockchain to ensure users are honest. This lecture provides an overview of how this system works.
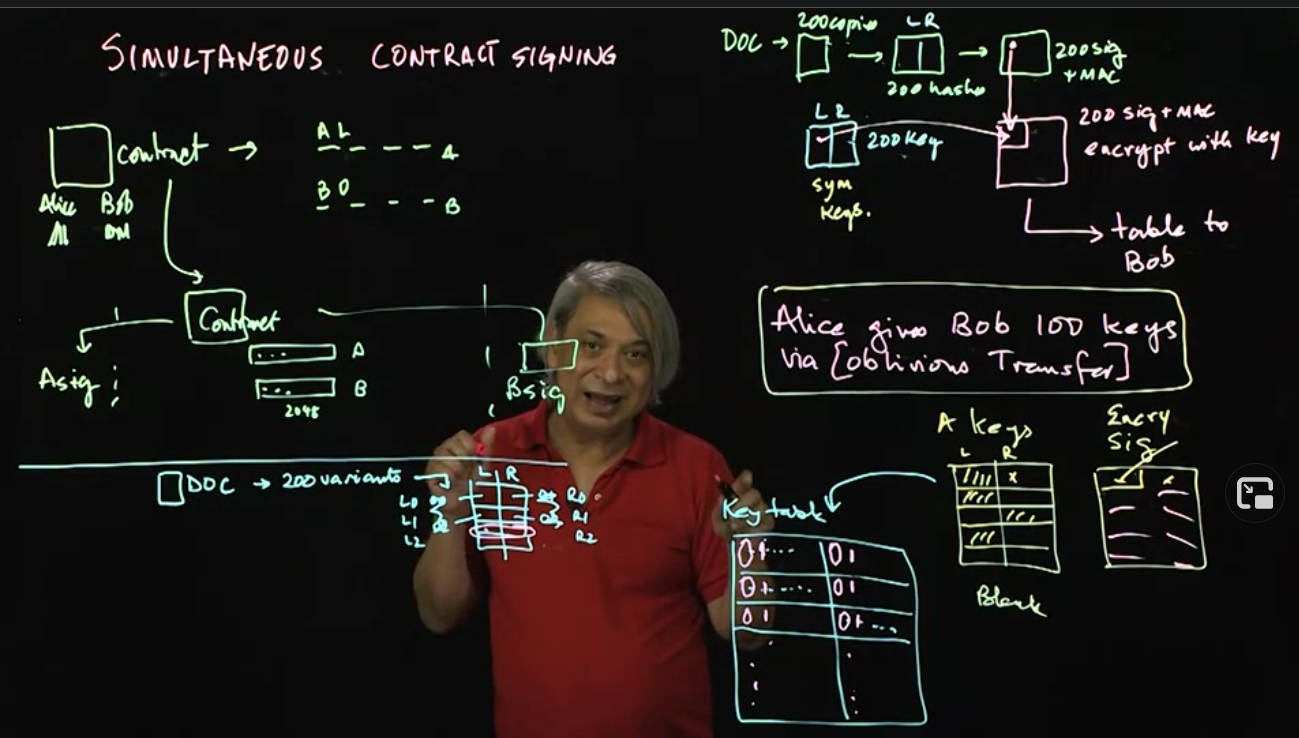
Simultaneous Contract Signing: Suppose Alice and Bob both need to sign a contract. Alice does not want to sign first, because then Bob could run away, leaving the contract unsigned. Using cryptography, they can sign simultaneously. This difficult protocol is necessary for building a digital cash protocol.
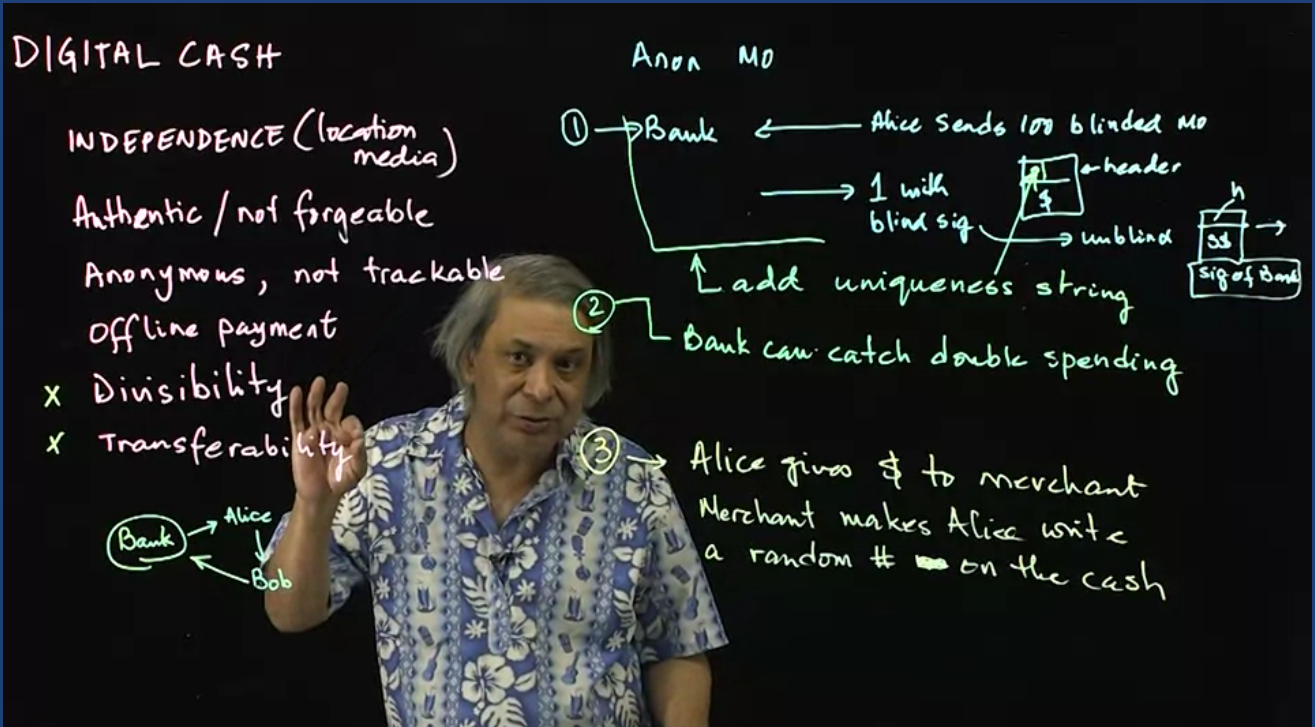
Digital Cash Protocols - Part 1 & 2:
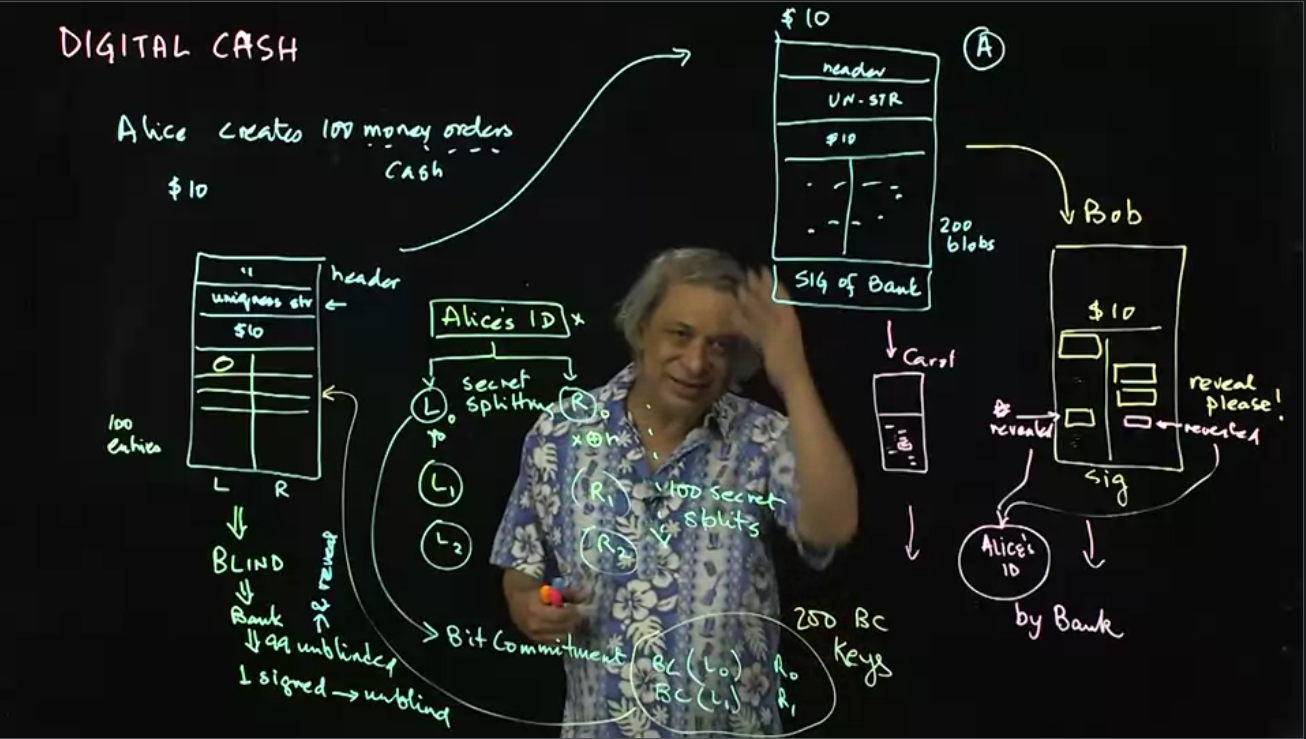
Digital cash, like paper money, is anonymous and can be used to transfer money between Alice and Bob without an internet connection. This intricate protocol is addressed in a two-part lecture.
Video 07: Digital Currency
Video 08: Bitcoin and Blockchain
Video 09: Simultaneous Contract Signing
Video 10: Digital Cash Protocols - Part 1
Video 11: Digital Cash Protocols - Part 2